Portuguese Banks Under Attack – Operation Magalenha Commences
When we speak about cybercrime, we have to mention how threat actors put a lot of thought into their campaigns. How they execute a certain attack determines its success. Campaigns can take months, but the operation we’re going to talk about now has been undergoing for years – Enter Operation Magalenha.

This campaign involves a potent, financially motivated group hacking group that has been targeting Portuguese financial institutions since 2021.
With many methods to distribute their malware to targets, these hackers appear to be very capable. How are they spreading this campaign? What institutions are in question? We’ll answer all your questions below.
Operation Magalenha: Years of Maliciousness
As we always mention, the methods used to infiltrate systems vary from one threat actor to another. Whether it’s phishing attacks, smishing, or vulnerability exploitation, everyone is at risk.
The Brazilian malware ecosystem is very well-known to include various financially-motivated groups. It has a rich history of targeting big companies in Europe in the past.
This particular campaign has been ongoing since 2021, initially relying on cloud service providers like DigitalOcean and Dropbox.
However, when the aforementioned firms elevated their policies and implemented strict rules on how their services are utilized, the Brazilian threat group had no other choice but to make a change.
They pivoted to TimeWeb – a popular Russia-based web hosting provider. This helps a lot with their campaign as it’s more of an extra obscure option.
The attacks mostly start with phishing emails masquerading as Energias de Portugal (EDP) and the Portuguese Tax and Customs Authority (AT).
This form of approach requires exquisite social engineering in order to successfully direct the victims to malicious websites that mimic these organizations.
At the end of this step, the ‘PeepingTitle’ backdoor will be injected onto the victim’s system following a five-second delay.
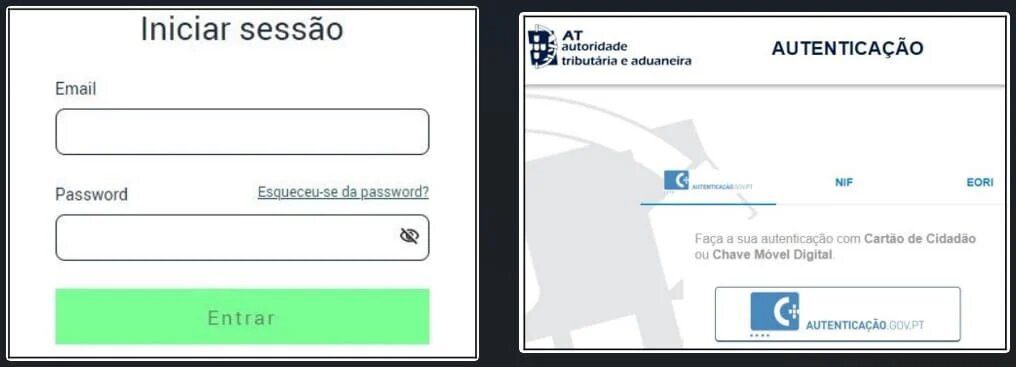
Once the backdoor is in place, it can perform all sorts of malicious practices, including monitoring the titles of application windows that have captured the mouse cursor. According to researchers:
“This is a simple, yet effective technique for evading static detection mechanisms – the scripts that are available on VirusTotal feature relatively low detection ratios.”
Source: Sentinel Labs
The main targets are users of Portuguese financial institutions, including government, government-backed, and private institutions.
We’re referring to the likes of Millennium BCP, ING, Banco BPI, ActivoBank, Caixa Geral de Depósitos, CaixaBank, Citibanamex, Santander, and Novobanco.
A Campaign Lasting for Years
Brazilian hackers are more than capable of successfully infiltrating systems all over the world. Now, their latest targets are Portugal and its financial institutions. Who knows what’s next?
Their operation is very well thought off, switching web hosts to avoid any campaign disruptions and operational difficulties. They’re dangerous, and all affected users should remain vigilant.





