PlugX Trojan – Fake Windows Debugger, Very Real “Full Control” Capabilities
Windows users have had their fair share of cyberattacks in the past few years. The problem is that, unlike macOS, any files can be downloaded on these platforms, making them susceptible to various forms of malware. Now, Windows is back in the spotlight, and it’s on the PlugX trojan’s radar.

Research shows that a fake Windows debugging tool called x64dbg is in the wild. Once installed, the PlugX takes root within the device and harvests sensitive information.
The trojan is not new and has done some malicious practices in the past. However, as researchers stated, it has gained new capabilities with recent updates. What do we know? Check the article below.
PlugX – Data Exfiltration at its Best
We’ve seen several malware families disguise themselves as legitimate applications to trick users into downloading them. Even Google Play Store has been witnessed hosting such apps in the past.
If Android’s most secure download hub couldn’t detect the infiltrations, how can a regular user do it while downloading an open-source file?
x64dbg is a popular debugger tool that Windows users operate frequently. In other words, the threat actors in this campaign know exactly what they’re doing by masquerading the PlugX trojan as this open-source software.
According to Trend Micro researchers Buddy Tancio, Jed Valderama, and Catherine Loveria’s report:
“This file is a legitimate open-source debugger tool for Windows that is generally used to examine kernel-mode and user-mode code, crash dumps, or CPU registers.”
That’s what x64dbg is used for. However, the main problem here is that x64dbg is a legit tool. Its valid digital signature can trick any security software, such as antiviruses. As a result, cybercriminals can roam freely without detection and execute their malicious intents hassle-free.
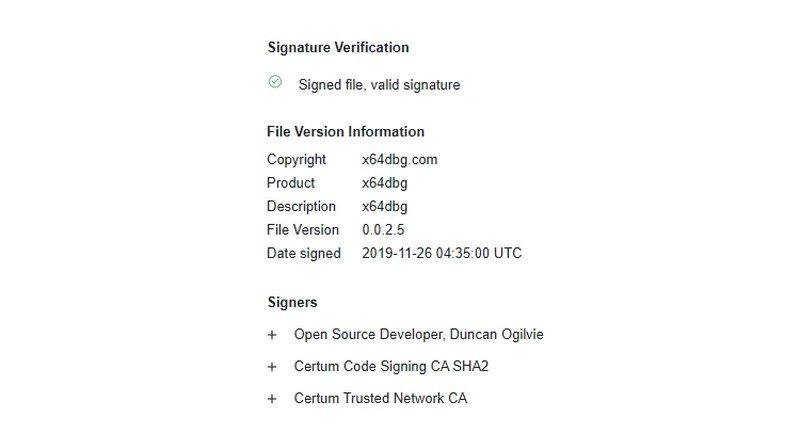
That’s how the PlugX remote access trojan has been masquerading as this legit tool to circumvent security protections in hopes of taking control of a target system.
For quite some time now, threat actors with a Chinese nexus as well as cybercrime groups, have been using the PlugX trojan. It started off as small, but the research shows huge advancement in the trojan’s activity.
“Despite advances in security technology, attackers continue to use [DLL side-loading] since it exploits a fundamental trust in legitimate applications.”
PlugX, aka, Korplug, has multiple functionalities, such as exfiltrating data and compromising a machine for various malicious actions, including taking full control of the device.
Not only that, but the malware can also hide malicious files on removable USB devices, which leads to the infection of other Windows hosts.
PlugX Returns – New Variant, Bigger Risk
Just like any trojan out there, PlugX poses a threat to users all around the world. Masquerading as a legit tool can fool a lot of individuals, which is why we always recommend staying vigilant when it comes to your downloads.
You never know what might be lurking in those files. Remember, it’s your personal information that is at risk. You have to take proper precautions if you wish to protect it from threat actors.





