We Are Symbiote – The Invisible Linux Malware
Infecting operating systems with malware is one of the ultimate ways for threat actors to infiltrate their victims’ devices. Whether it’s PC, Mac, Android, Linux, or iOS, hackers will find a way to get in. Once the malware is detected, security firms analyze everything there is to it. But what if it’s dubbed as “virtually invisible to detection by live forensics”? Yeah, such malware exists in the form of SYMBIOTE.

Security firms all over the world specialize in various domains when it comes to malware. However, when the malware itself is an unusual piece that required Intezer security researcher Joakim Kennedy, BlackBerry Threat Research, as well as Intelligence Team to figure it out.
The researchers state that this is unlike anything they’ve seen before. It first hijacks and then infects every single running process. The Symbiote malware is dangerous, and we’re here to discuss everything about it.
Symbiote – An Ultimate Cyber Parasite
Linux’s history with malware is quite known. Normally, when malware infects a Linux device, it sets root within the system and attempts to compromise running processes.
Symbiote works in another way. Just like everybody’s favorite symbiote (Venom) in the MCU, the malware got the name due to its parasitic attributes. It instead acts as a shared object (SO) library, which further loads itself on all running processes via LD_PRELOAD.
Back in 2021, attackers developed and used Symbiote to target financial institutions in Latin America. And based on its nature, the malware is hard to detect and considered to be very evasive.
That’s why researchers are not very certain whether it’s targeting specific victims or just broadly hitting any target it sets its sight on.
As we mentioned, Symbiote acts like a Shared Object library. Once it “parasitically” compromises a target machine and embeds itself within the system, it can give full rootkit functionality to its operators.
So, how is Symbiote hiding its presence? Aside from hooking libc and libpcap functions, the malware makes use of the extended Berkeley Packet Filter (eBPF) feature.
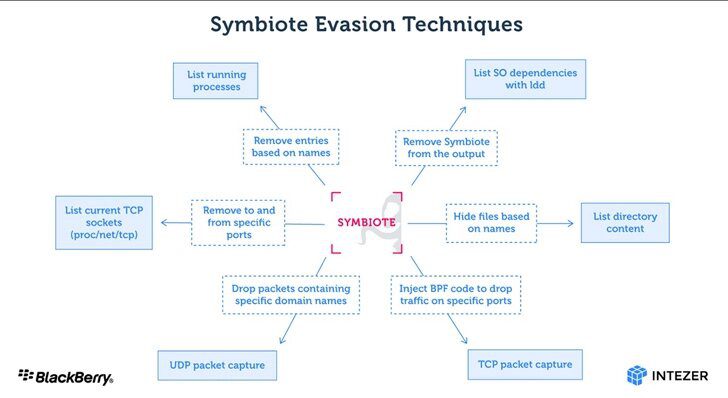
It does that by embedding itself into an inspection software’s process. Once it does that, it uses the BPF feature to hand-pick results that would showcase its malicious activities. According to the researchers:
“Since the malware operates as a user-land level rootkit, detecting an infection may be difficult. Network telemetry can be used to detect anomalous DNS requests and security tools such as AVs and EDRs should be statically linked to ensure they are not ‘infected’ by userland rootkits.”
Blackberry shared more information about the process. You can see the full analysis on their official blog page.
Symbiote Malware – The Invisible Linux Parasite
Just like any other malware, Symbiote is very dangerous. Regardless if it’s detectable or not, you can never let your guard down, especially if you’re a Linux user.
Our website presents the best guides to protect your privacy. Make sure to give them a quick read as your private information is at risk.
If it took several security firms to analyze this, you should get an idea about how impactful it can be. Don’t click on any link you get via email or text. Never trust sources you find shade. Watch out, and always stay safe.





