From Flu to Tea – The Ultimate Bot Collaboration Targets Android
Android devices don’t seem to catch a break when it comes to cyber-attacks. In fact, aside from being a constant target, there’s one malware that’s kind of hell-bent on infecting the OS.

Flubot has been targeting Android for quite some time now. However, recently, researchers spotted yet another malware that goes by the name of Teabot.
With two highly dangerous malware campaigns, Android users seem to be outnumbered, considering each one of these bots attacks in a different way.
Flubot and Teabot make the perfect combination for a cyberattack and we’re here to shed more light on the matter. Make sure you give this article a good read and learn all about the new phishing tactic.
The Tea to the Flu: The Ultimate Malware Tag-Team
Flubot has been around targeting Android users for a while now. In fact, not long ago, the malware was impersonating a Flash Player upgrade.
Using typical smishing lures or laced apps against Android users, such malware can easily infiltrate the device, harvest any data it’s designed to collect, and commit all sorts of malicious acts.
Now, two campaigns are designed specifically for Android devices, involving the notorious Flubot and another that goes by the name of Teabot.
Apparently, both malware campaigns are concentrating on users in Australia, Germany, Poland, Spain, and Romania. While the destination is pretty common, Teabot and Flubot infect Android devices in a different matter.
Flubot uses phishing SMS messages, including courier messages, “Is this you in this video?” coaxes, browser updates, voicemail notifications, or application updates.
Back in December 2021, Bitdefender Labs intercepted a Flubot campaign with over 100,000 malicious SMS, showcasing the massive volume of its distribution.
Why does it have that much impact? Well, once the malware infects a device, it uses the victim’s contact list to send other SMS lures. And since a contact list reflects trust between contacts, better distribution is guaranteed.
Round 2: Teabot
Teabot, on the other hand, operates using none other than the official Google Play Store. It infiltrated unsuspecting victims’ devices via trojanized apps on Google Play. We’ve listed some of the apps below:
- Smart Cleaner – 1,000 downloads
- Weather Cast – 10,000 downloads
- QR Scanner APK – 10,000 downloads
- QR Code Scan – 10,000 downloads
- Weather Daily – 10,000 downloads
- QR Code Reader – Scanner App – 100,000 downloads
The applications above featured no malicious functionality, which helped fool Google Play Store’s review process and reach a wider number of Android users.
As we mentioned, the campaigns are targeting specific countries. When the victim downloads and executes any of these apps, they start a background service that examines the country code.
If the user is residing in countries such as Ukraine, Uzbekistan, Uruguay, or the United States, everything stops immediately.
Finally, with the select victims, the app gets an APK from a GitHub repository, containing the TeaBot variant. Not to mention that it asks the user to allow third-party sources to install packages.
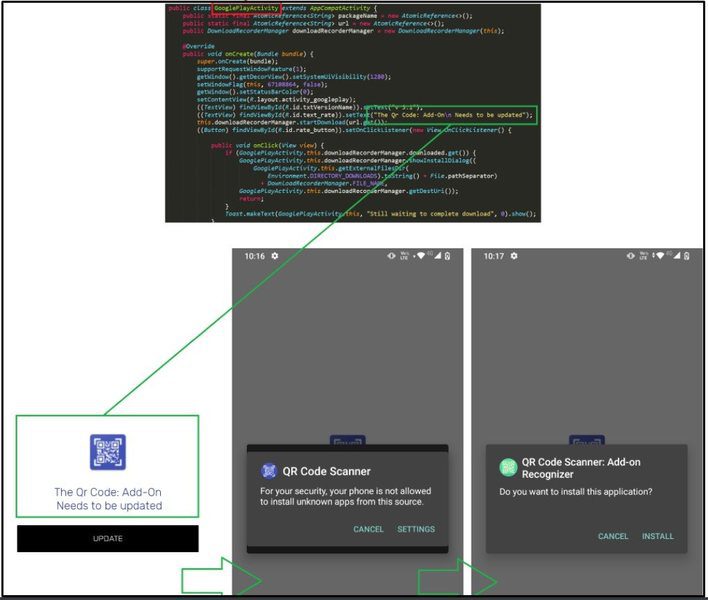
According to BitDefender, around 17 different versions of TeaBot have been infecting Android devices through the listed apps. And just like many other trojans, Teabot solidifies the following statement: Even if you’re installing applications from Google Play Store, you’re not always safe.
Flubot and Teabot – Malware Everywhere
Whatever your source is, we always advise you remain vigilant with your installations. Make sure that you go through everything there is to check including ratings, user reviews, and if possible, some expert reviews.
Other than that, always check what permissions the app is asking for. And if the app is already downloaded, monitor your data usage and device battery very carefully.
Finally, make sure you have a reputable anti-virus tool on your device. That way, if there’s anything lurking around, you would know and get rid of it before it’s too late.





