Clipboard-Hijacking Campaign: Trojanized Tor Browsers Taking Over
Are you a privacy-savvy individual? Do you use Tor Browser to further elevate your online privacy? Then you must give this a read. Using fake applications to spread malware has become a common tactic among cybercriminals. And now, they’re doing so with trojanized versions of the popular Tor Browser.

This particular campaign involves injecting clipboard-hijacking malware into the victims’ devices. The cybercriminals’ goal is clear – steal users’ cryptocurrency transactions.
Apparently, the threat actors behind this campaign are targeting countries all over the world. However, it seems that their main focus goes on Russians and Eastern Europeans. Here’s everything we know about this dangerous attack.
Fake Tor Browser – For Russia with Maliciousness
When we talk about the Tor Browser, we’re immediately referring to users who prefer surfing the web anonymously. In fact, that’s exactly what the browser specializes in, as it hides the user’s IP address and encrypts his/her traffic.
Unfortunately, these very effective “Positive” features are used by some individuals to access illegal dark web market services that cannot be visited through regular search engines and browsers.
On the dark web, users/buyers/sellers purchase their “Goods” with cryptocurrency – mainly for privacy/anonymity reasons. Now, that’s exactly what cybercriminals are preying on.
The campaign does focus on Russia, but why? The country banned Tor, but it also harnesses the second largest number of Tor users – 15% of all Tor users. According to Kaspersky:
“We relate this to the ban of Tor Project’s website in Russia at the end of 2021, which was reported by the Tor Project itself.
According to the latter, Russia was the second largest country by number of Tor users in 2021 (with over 300,000 daily users, or 15% of all Tor users).”
Cybercriminals are promoting this fake software as a strengthened Tor Browser in terms of privacy and security. With Tor being prohibited in Russia, the threat actors saw this as an opportunity since the official version is harder to download.
Not only that, but they also added an extra feature that allows users to choose their preferred language.
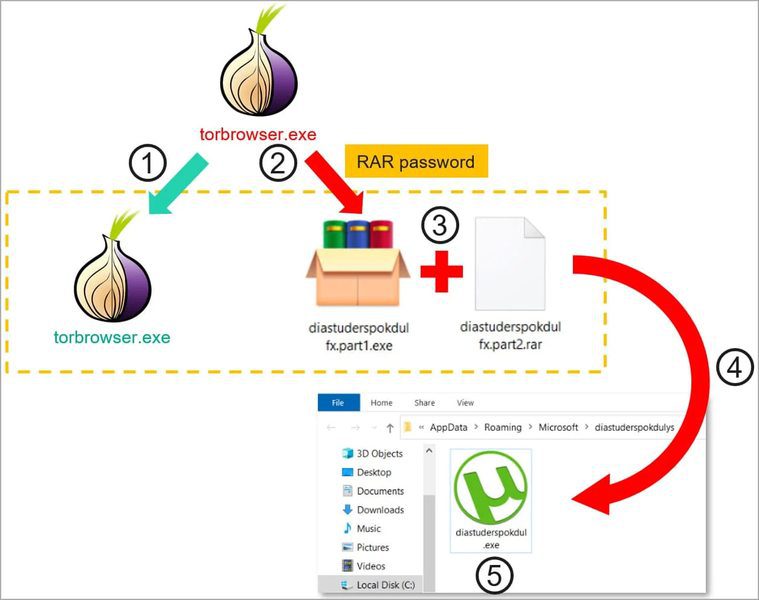
Once the users download and install the fake Tor Browser, the malicious practice begins. Tor will launch normally. However, in the background, the archive extracts the malware and initiates it as a new process while registering it on the system autostart.
As a disguise, the malware takes on a uTorrent icon. Is there a better way to hide its existence? We don’t think so.
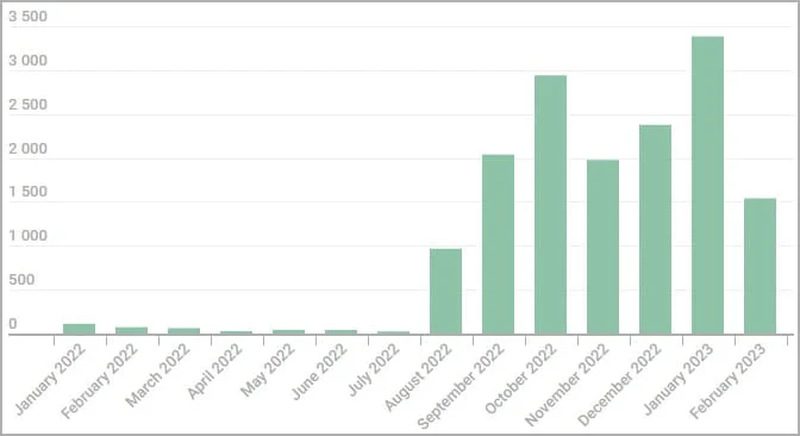
As we mentioned, the majority of these fake Tor browsers have been found in Russia and Eastern Europe. But the attack is much bigger than that.
The threat actors are also spreading these trojanized versions in the United States, Germany, China, France, the Netherlands, and the UK.
When it comes to cryptocurrency addresses, copying them to the clipboard and pasting them into another software/website is a common practice as they’re hard to memorize.
The malware examines those addresses and replaces them with an associated cryptocurrency address that the threat actor operates. As a result, the sent transaction gets harvested.
Another Campaign, Same Old Elevated Practices
Kaspersky’s report shows a lot in terms of how dangerous this malware campaign is. Apparently, the threat actors are operating thousands of addresses on each malware sample, which makes wallet tracking, reporting, and banning extra difficult.
As we always say, never trust ads or any other source than the official one. If you want to download the Tor Browser, you can manually only install the software from the official website. Your data is at risk – Stay safe.




