The Venus Ransomware: An Out-of-This-World Malicious Campaign
Ransomware attacks are on the rise, targetting vulnerable systems all over the world. A while ago, we witnessed how impactful 0mega ransomware was with its double extortion technique. Now, the newly created Venus ransomware is striking and encrypting victim files worldwide.
The ransomware began its operations back in August 2022, which makes it relatively new. However, much like its name “Venus,” its capabilities are definitely out of this world.
Apparently, the threat actors behind this campaign are targeting publicly-exposed Remote Desktop services, but there’s more to it. Here’s everything we know.
You’re Locked Out – The Dreadful .venus Extension
As we mentioned, the number of ransomware attacks is exceeding that of those that occurred in the past couple of years. This led cybersecurity firms to come up with various solutions, including the creation of unique decryption tools.
Speaking of decryption, Avast manufactured a tool that decrypts files affected by the several variants of the Hades ransomware. Unfortunately, since Venus is still new, there’s no workaround if the attackers managed to get a hold of your files.
The campaign saw the light when Linuxct contacted MalwareHunterTeam in hopes of shedding some light on the matter. Here’s how the conversation went:
@malwrhunterteam Hey, do you have any details about ‘Venus’ ransomware (not VenusLocker, extension is .venus instead of .venusf). Infection happened via RDP. Can give more details in DM if wanted.
— linuxct (@linuxct) October 6, 2022
Linuxct stated that the threat actors gained access to a victim’s corporate network via the Windows Remote Desktop protocol. So how does it work?
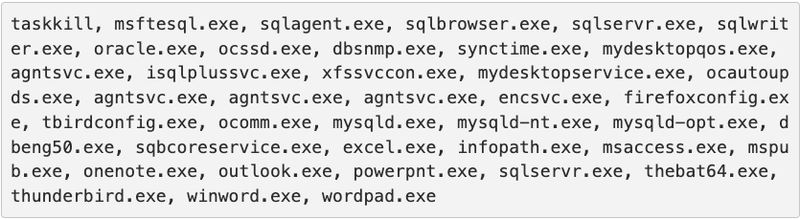
Apparently, when the attackers execute Venus, the ransomware will attempt to terminate thirty-nine processes associated with Microsoft Office applications and database servers.
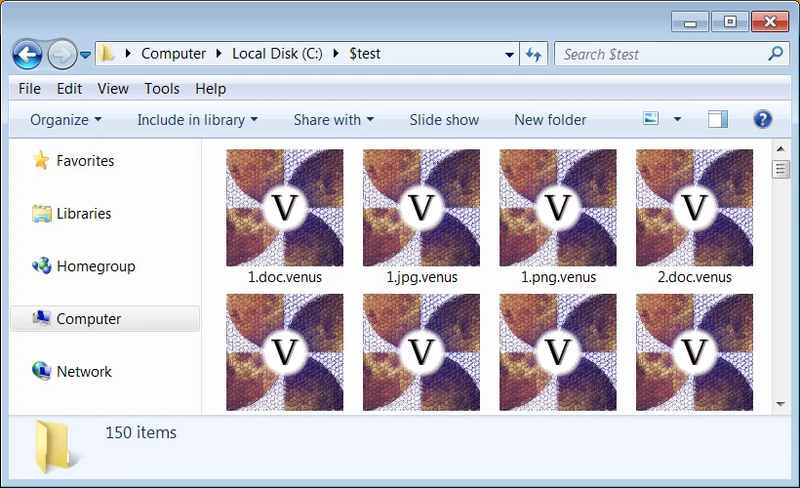
Now, just like almost every single ransomware out there, the format of the file changes once encrypted. Also, it resembles the name of the ransomware that hit it. In Venus’ case, it’s will append the .venus extension, as shown below.
So basically, when a ransomware attack is executed, it creates an HTA ransom note in the folder that will automatically be displayed when the encryption process is finalized. It’s no different in Venus’ case:
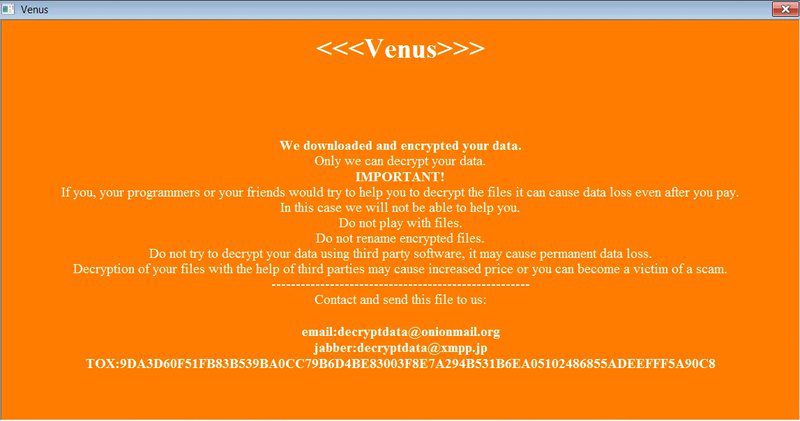
In the image above, Venus included a TOX address and email address that the victims can use to contact the attacker in order to start the ransom payment negotiations.
The ransom note also includes base64 encoded blob, which may likely be an encrypted decryption key. The victims would receive it once the payment is settled.
Venus Ransomware – Use a VPN
Although it’s still relatively new, the Venus ransomware is fairly active. According to the research, this ransomware campaign is very dangerous, especially to those who take online security lightly.
The ransomware targets publicly-exposed Remote Desktop services, so it is crucial to put these services behind a firewall. Aside from that, you should never expose Remote Desktop Services on the internet – the use of a Virtual Private Network is always recommended.





