You Have a New Voicemail – A Cliche, but Effective Phishing Attack
Phishing emails mainly revolve around victims clicking on fake links within fake emails. It’s as simple as that, but the aftermath is devastating. “You have a New Voicemail or Voice Message” campaigns have been used a lot, which should be ineffective by now. Unfortunately, that’s not the case.

A lot of users still fall victim to this scam, and the latest campaign shows exactly that. This time around, the targets are those who use Office 365.
The attackers send them voicemail notification messages with malicious attachments in hopes of stealing their credentials. How is this message reaching its victims? We’ve explained everything below.
A Voicemail Better Left Unheard
Phishing attacks are on the rise and they have reached new heights in the last couple of months. Based on recent reports, Office 365 represents one of the most commonly used email clients.
It has around 60 million commercial users and 50,000 small business customers globally. When it comes to phishing attacks, every day, around 15 billion spam emails make their way across the internet.
With such a high number, spam filters will no longer function correctly, or keep up with the numbers. They’re bound to slip up and miss a few.
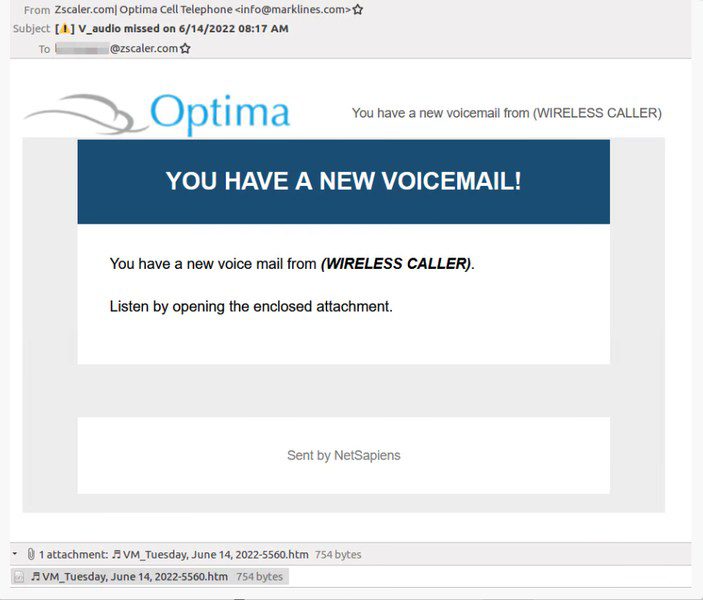
And Voicemail phishing attacks are probably the most popular among those. The recent attack sees the threat actor sending emails that include a voicemail notification.
It tells the victim that they have a missed voicemail and lures them into opening a malicious attachment. It’s quite clear below that the attack has put a lot of work into this. Even the “From” email mimics the one of the victim’s organization.
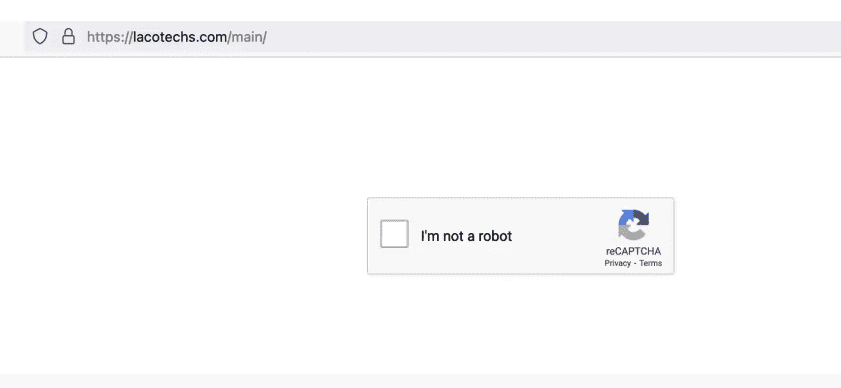
According to the study done by researchers at ZScaler, the threat actor leveraged email servers located in Japan. To make this attack more effective, the attackers added a CAPTCHA process.
Not only does this allow the threat actor to avoid automated URL analysis tools, but it also makes sure that no bots will have further access.
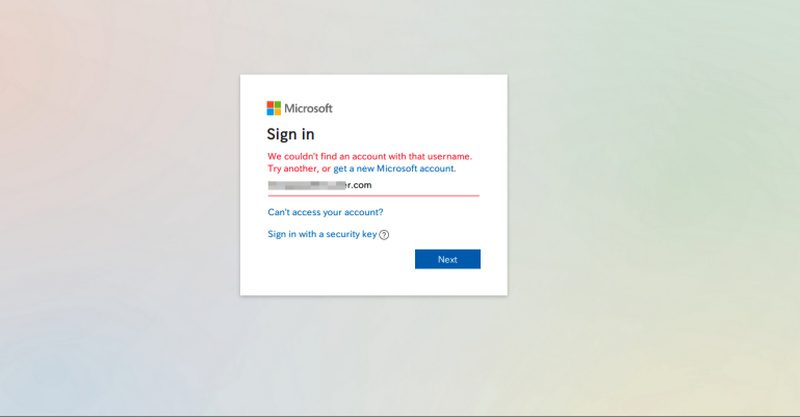
Finally, once the users solve the reCAPTCHA section, they will head to the final credential phishing page. This is where the page prompts them to submit their credentials and steal them in the process.
So far, the researchers found out that this attack is targeting organizations in the US military. Not only that, but supply-chain organizations in manufacturing and shipping, security software developers and providers, and healthcare and pharmaceutical have also received their fair share of phishing emails.
Voicemail Phishing Attack – One Click Does it All
Phishing attacks that include this voicemail scam have proven to be successful over the years. Unfortunately, a lot of individuals keep falling for this trick, which makes it very dangerous.
The first thing you need to do to avoid this predicament is not to click on any shady link you come across in an email. If it’s your organization, make sure to visit the website manually.
Second, enable two-factor authentication. That way, if the threat actor used your credentials, you’ll receive a text message as a warning that your credentials have been compromised.





