Uber’s Major Vulnerability – 57 Million Customers at Risk
When we speak of vulnerabilities, we also have to talk about their exploitations. Hackers and threat actors prey on such incidents to commit their malicious acts, regardless of the casualties. Unfortunately, this time, the number is big, as 57 million Uber customers are the main targets.

A vulnerability can occur in any department, and with Uber, it’s in the email system. This so-called bug allows just about anyone to send emails on behalf of Uber – not a fake one, an actual legit email.
Threat actors could target all 57 million of Uber’s customers and commit all sorts of malicious practices, including credit card theft and more. So, what is this bug? How did Uber react (Not what you’d expect)? Find out in the article below.
Uber Vulnerability – Your Ride is Here (Or is It?)
When users receive an official email from Uber, they’re more likely to reply without having to think twice. Phishing emails are definitely on the rise.
However, while threat actors usually go to great lengths trying to fake logos in hopes of legitimizing an email as much as they can, this Uber vulnerability makes their job a lot easier.
According to Seif Elsallamy – a security researcher and bug bounty hunter, this bug allows anyone to send emails on behalf of Uber. Yeah, using the official company name.
Nothing fake at all, because, well, they’re not. Whatever email provider the victims are using, it won’t figure out that this is not Uber as the email is going to make it past any spam filters.
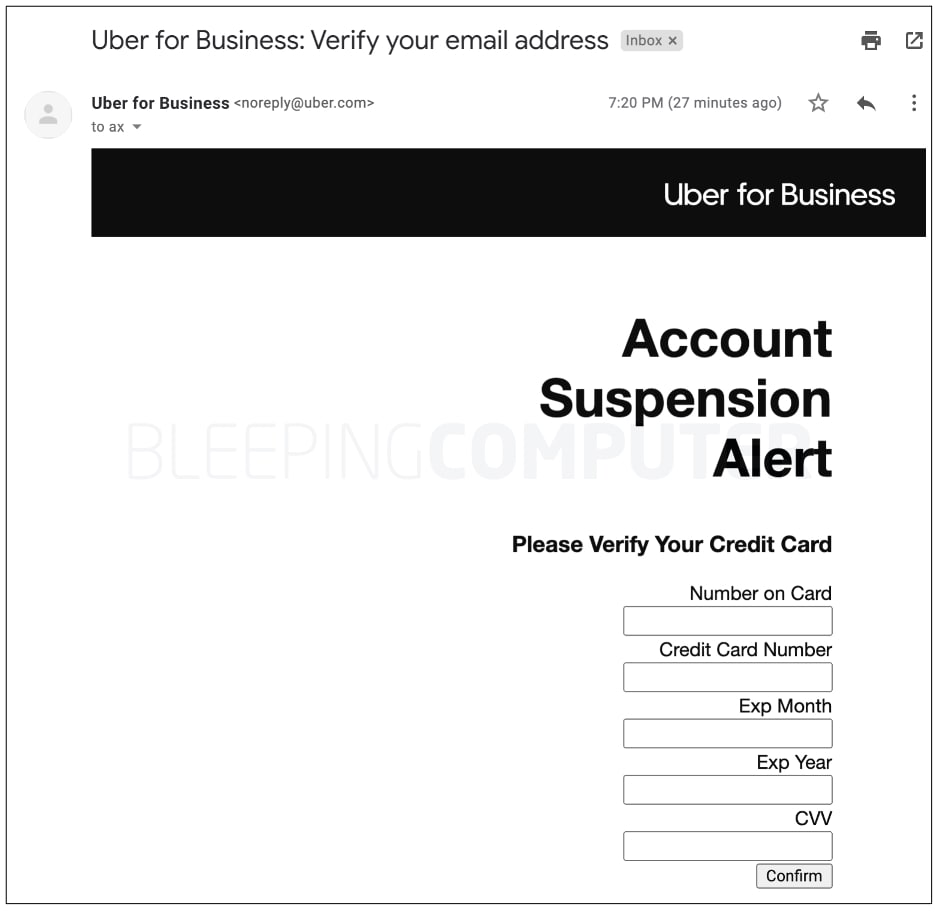
Elsallamy demonstrated what exploiting the bug can lead to, so he tested it with Bleeping Computer. He sent them an email message that, of course, came from Uber itself. As reported, it landed in their inbox, not in the Junk folder:
As seen in the image on the left, the email is clearly coming from Uber. What makes this dangerous is that it can include anything, such as a “verify your credit card” notification.
If the information is submitted, everything would be sent to a test site set up by the attacker – as reported by the researcher. To solidify his point, he left a message at the end of the email as a disclaimer: “This is a security vulnerability Proof of Concept.”
The Ugly Truth – Reported, yet Rejected
When a reputable company receives a minor complaint, it does its best to resolve it. Well, at least that usually happens. Unfortunately, this is not minor, and this is not how it went down.
Seif Elsallamy could’ve left the matter unintended, but he didn’t. Instead, he responsibly reported the vulnerability to Uber on New Year’s Eve of 2021 via the company’s HackerOne bug bounty program.
With such a bug, you’d think that Uber would go all hands on deck to fix it, but that wasn’t the case. The company rejected Elsallamy’s report for being “out-of-scope,” assuming that exploiting the flaw would require social engineering.
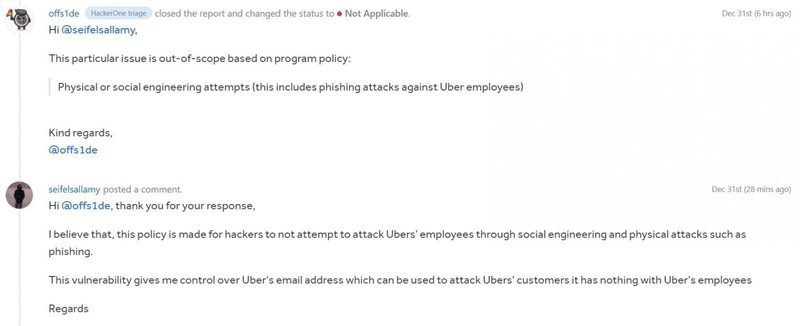
The worst part about this is that it’s not the first time such a vulnerability has been ignored. Apparently, in the past, bug bounty hunters Soufiane el Habti and Shiva Maharaj reported the issue but were met with nothing but rejection as well.
Uber’s Vulnerability – Not a Safe Ride!
The flaw is an exposed endpoint on Uber’s servers and it allows anyone to craft an email on behalf of Uber. Aside from the researcher, BleepingComputer also contacted Uber but has not heard back yet.
This problem is huge as it compromises more than 57 million customers. Uber should know how serious this is, and acknowledge the consequences this might bring along the way.
For now, be very careful when you receive an email from Uber. If you have doubts, try contacting the company directly – don’t submit any personal information.