A New Phishing Campaign – Zimbra Users Beware!
Phishing attacks, i.e., luring victims with bait that looks trustworthy, have become a popular tactic among cybercriminals. There are several ways such techniques can be implemented, and a fake email is the most common one. That’s exactly the case recently, as threat actors are spreading fake emails in an attempt to steal credentials for Zimbra Collaboration email servers worldwide.

The “I Zimbra by Talking Heads”-inspired platform has become quite popular among users all over the world. This makes it the perfect disguise for cybercriminals to initiate a phishing attack.
Apparently, they’re sending fake emails with malicious attachments to organizations worldwide. However, there doesn’t seem to be any specific target – every company is at risk.
How is this campaign being implemented? What are the threat actors after? Find out in the following article.
The Zimbra Phishing Campaign – One Click, One Devastating Outcome
When it comes to phishing attacks, threat actors target those whose information can benefit them the most.
In fact, this year has seen its fair share of such attacks, where cybercriminals impersonate a very known company to trick victims into doing exactly what they want them to.
A while back, RomCom Hackers used this particular tactic to target NATO Summit Attendees. Even before that, threat actors used phishing campaigns to spread the Horabot malware in hopes of taking control of the victim’s Gmail and Outlook accounts.
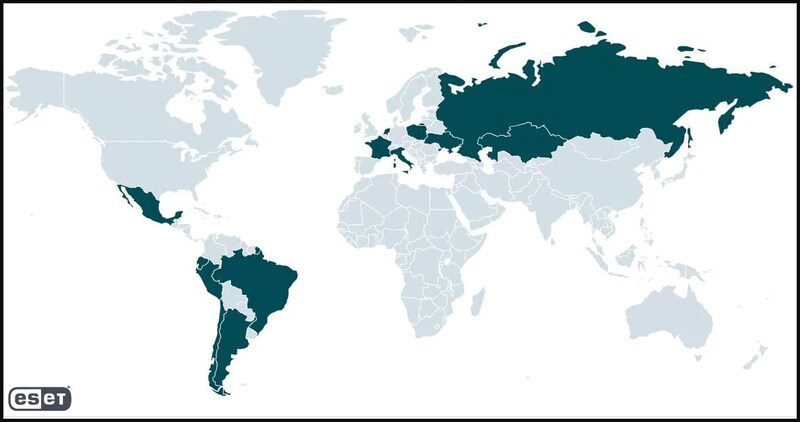
Now, the individuals behind this campaign are using urgency to target their victims. How? First of all, this attack is not focused on a specific country as others do. It’s global, as seen in the following map.
As with most phishing attacks, this one kicks off with an email that induces some sort of urgency to force the victims into acting hastily.
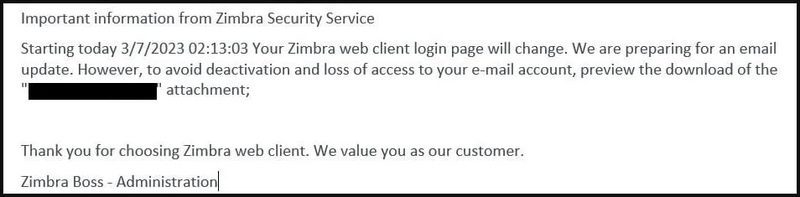
The Bogus Email!
The email claims that Zimbra will be implementing an imminent email server update, which may result in temporary account deactivation.
Within the email, there’s an attached HTML file that’s “Supposedly” there if the recipient wants to learn more about this upgrade and how to avoid the deactivation of his/her account.
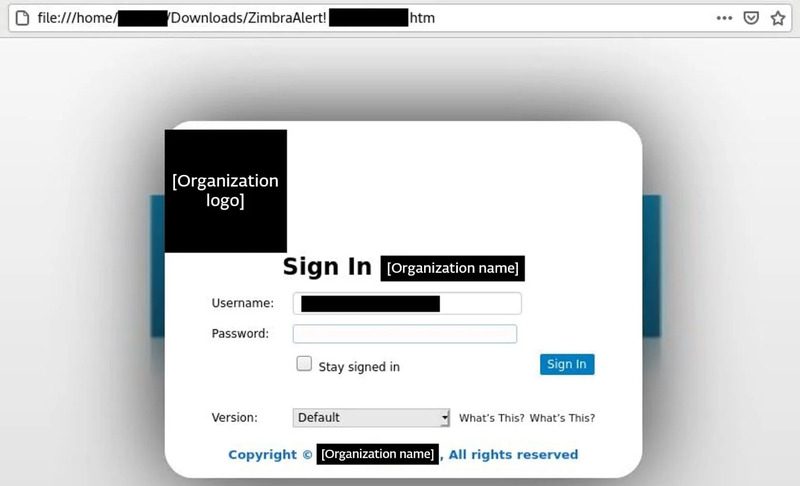
When the users click on the link, it’ll redirect them to a fake Zimbra login page that looks exactly the same. Even the logo and brand appear to be very convincing.
One thing that actually piqued our interest is the fact that the login form will be prefilled. If that doesn’t give legitimacy to this campaign, we don’t know what will.
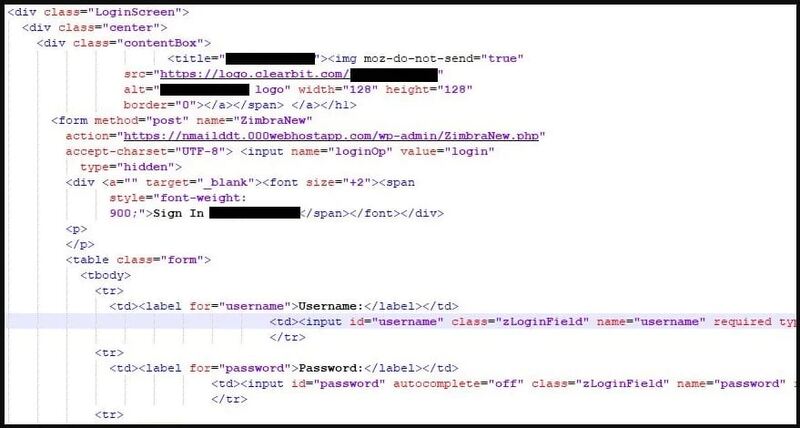
And we all know what happens next. When the users submit their account passwords, they are directly sent to the threat actor’s server via an HTTPS POST request. The image below shows how the process goes:
Unfortunately, it doesn’t end here. According to ESET, once the threat actors take control of a certain email within the organization, they can also spread phishing emails to other members within it.
New Phishing Campaign, Same Old Tactics
Zimbra Collaboration email servers reflect a valuable target for threat actors for various reasons. One of them is to collect internal communications and gather as much information as possible.
Zimbra is a huge name in the industry, and cybercriminals can benefit a lot from a breach within its systems. When it comes to phishing attacks, the most important rule is to treat every email as a malicious one.
Don’t click on random links. If there’s anything you need to know, you can manually visit the desired source’s page. Stay safe.





