APT36 Hacking Group is Back – YouTube Clones Everywhere
YouTube is by far the most popular streaming platform in the world, and threat actors are well aware of that. The service has been used in the past to deliver malware, but this time around, apps that mimic it are in the spotlight – Enter APT36 hacking group with a new malicious campaign.

APT36, aka Transparent Tribe, has been around for quite some time now, wreaking havoc among internet users. Now, they’re using at least three YouTube clones, installed via APK, to deliver their signature remote access trojan (RAT), CapraRAT.
The group is well known to target entities of Indian defense and government. What is their goal in this recent attack? How are they pulling it off? We’ve discussed everything below.
Transparent Tribe – A Malicious Binging Experience
As we mentioned, YouTube is considered to be the number one place users tend to visit when they’re looking for some binge-viewing to kill time.
Only second to Facebook, YouTube is the second biggest social media in the world, with over 2.7 billion active users.
Let’s face it – YouTube has everything one needs for entertainment – Gamers can also find channels that cater to their interest.
Unfortunately, such popularity can also be concerning, as cybercriminals would definitely target a platform with so many users; it just makes the job easier.
In fact, this isn’t the first time YouTube was used maliciously. Well, a while back, a “major” malvertising campaign saw threat actors create YouTube ads that show up whenever “YouTube” keywords were submitted on top of the search results.
This time around, the hacking group APT36 is spreading Android apps that mimic YouTube in design and functionality, but instead infect users with CapraRAT trojan.
Enter the Fake Apps
“YouTube” and “Piya Sharma” reflect two of the apps in question. These fake applications might resemble YouTube, but users can easily notice the difference.
These fake platforms resemble YouTube when launched within a browser. This should be the first indication that they’re fake.
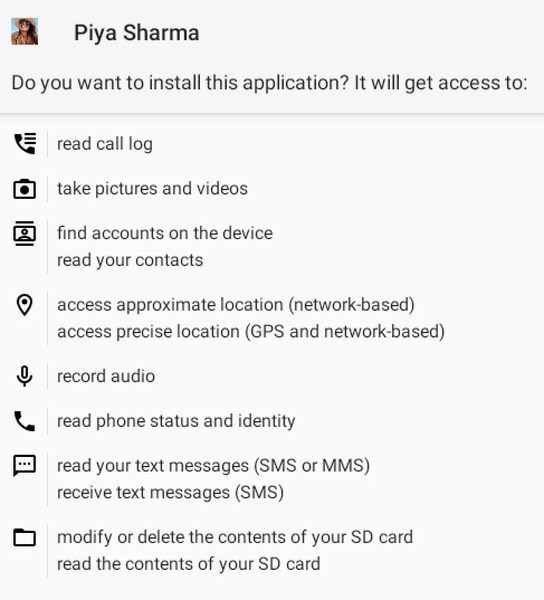
Another indication is the fact that these apps ask for unnecessary permissions. YouTube would never ask for permissions, such as taking pictures/videos, reading call logs, and the like.
When the applications take root on the device, they’ll inject the CapraRAT trojan – Transparent Tribe’s signature malware. According to SentinalLabs, this particular Trojan is capable of the following:
- Recording with the microphone, front & rear cameras
- Collecting SMS and multimedia message contents, call logs
- Sending SMS messages, blocking incoming SMS
- Initiating phone calls
- Taking screen captures
- Overriding system settings such as GPS & Network
- Modifying files on the phone’s filesystem
In other words, CapraRAT grants the threat actors control over much of the data on the Android devices that it infects.
You don’t want your data to be exposed in this matter. Transparent Tribe is persistent, and it’s obvious with its constant creation of new applications. Be careful.
APT36 Returns – Users in India and Pakistan Beware!
The Transparent Tribe hacking group seems resilient to target users in India and Pakistan. They’ve been around for quite some time now, and they don’t seem to be stopping any time soon.
Users, we urge you to only download your content through official sources. If you want an app, get it via Google Play Store. Don’t go searching for it via APKs. Stay Safe!





