DarkTortilla’s Phishing Attack – One Malware, Several Dropped Trojans
Cyberattacks can come in all forms, and with the right tools and expertise, they can do a lot of damage. So, imagine if a certain group has been around since 2015 – can you predict the impact of any campaign they launch? That’s exactly the case now, as DarkTortilla has resurfaced to spread multiple stealers and Remote Access Trojans (RATs) via phishing attacks.

Over the years, companies and individuals have fallen victim to cyberattacks by both new and well-known threat actors. The DarkTortilla malware can do a lot, especially while impersonating reputable entities such as Grammarly and Cisco.
Users are receiving bogus emails and ads that redirect them to phishing sites where the malware is present. What can DarkTortilla do? How is the entire process executed? Find out below.
DarkTortilla – Enter Fake Grammarly and Cisco
We’ve seen numerous threat actors masquerade their operations as legitimate brands to fool their victims. When it comes to phishing, a lot of factors should be considered by the operators to guarantee high success rates.
For example, a while ago, a phishing campaign included urgent emails that called for immediate action. They used the sense of emergency to trick the users into following the provided link.
Now, we can’t say the same situation is at hand. In fact, they’re just sending emails impersonating legitimate Grammarly and Cisco sites to lure victims and trick them into downloading the DarkTortilla malware.
It all starts with an email or a fake pop-up ad. If the victim happens to encounter the Grammarly version, this is what he/she gets:
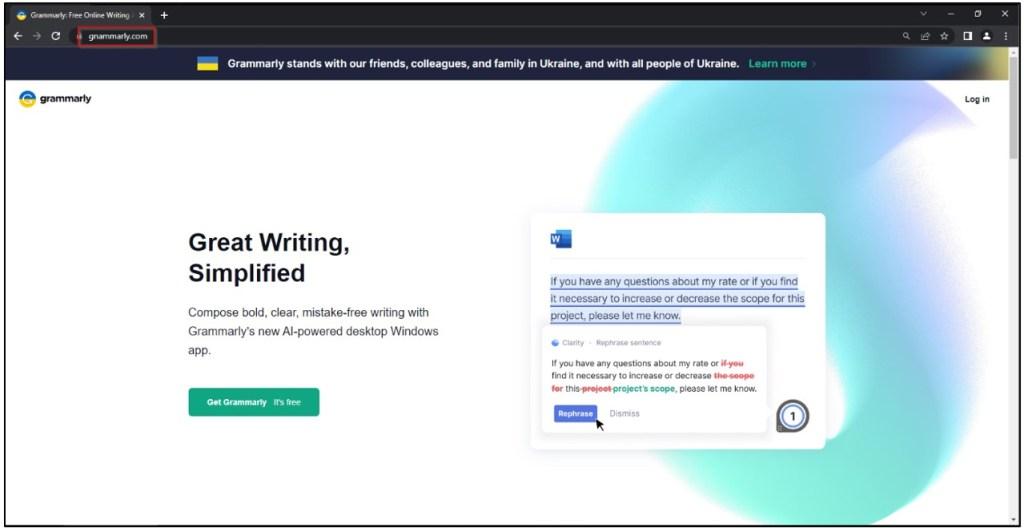
The legitimate Grammarly is free, and the fact that the fake website states it may attract a lot of users. Once they users click on download, they’ll infect their devices with the DarkTortilla malware.
It gets worse. This variant of the malware is upgraded. Once it takes root, it’ll drop several Remote Access Trojans such as AgentTesla, AsyncRAT, and NanoCore. Here’s what Cyble had to say about the malware’s practice:
“Based on the technical analysis, the Grammarly phishing site downloads a malicious zip file named “GnammanlyInstaller.zip” when the user clicks on the “Get Grammarly” Button.
The zip file further contains a malicious cabinet file, “GnammanlyInstaller.ce9rah8baddwd7jse1ovd0e01.exe” disguising itself as a Grammarly executable.”
The other phishing attack impersonates one of the biggest companies in the world, Cisco. With this one, the threat actors have also concocted a fake website that masquerades as a legit Cisco page.
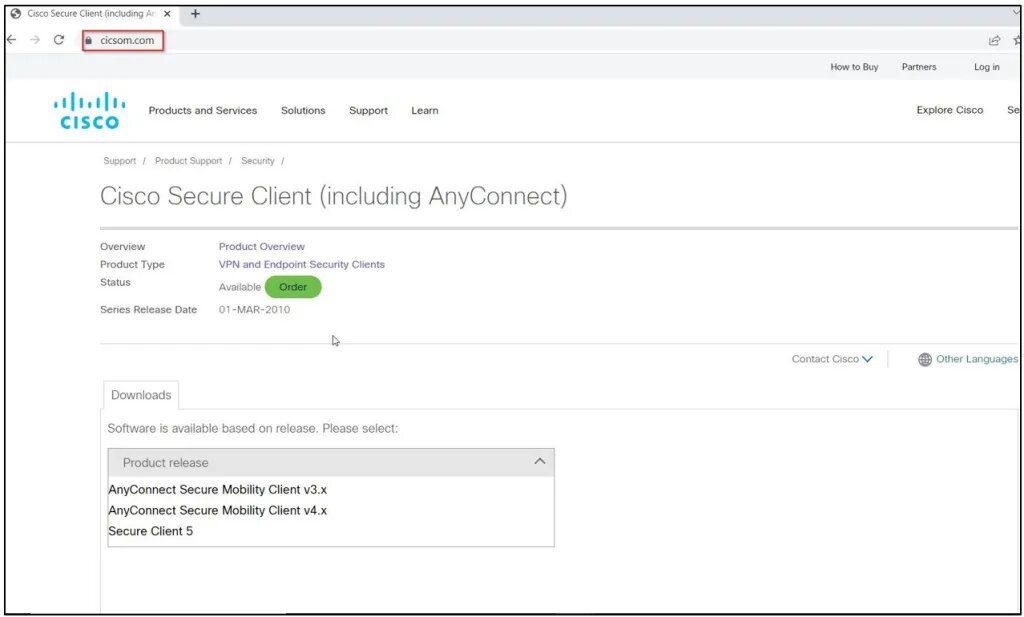
The malware is dangerous, especially due to the fact that it can execute additional malicious operations. Not only that, but it has the capability to evade anti-virus detection.
To avoid such predicaments, make sure not to open any suspicious links embedded in emails. Aside from that, stick to downloading your applications from trusted sources and install a reputable anti-virus.
An Unappetizing Phishing Scam
When it comes to phishing attacks, your awareness of the subject matters – If you know you’re being scammed, you won’t end up as a victim in the end.
Treat every email as if it’s a phishing one, and never click on a provided link. If there’s a task you need to do, make sure to visit the official source and do it manually.
Shortcuts, especially in emails, can lead to malicious catastrophes. Be careful, stay vigilant, and keep your data completely safe.





