Another Accomplishment – Cybersecurity Firm Launches “Free Key” Ransomware Decryptor
The battle between cybersecurity firms and malicious groups will never end. As long as there are actors targeting individuals with malware, ransomware, and the like, security firms will always be there to save the day. Big names like Avast created ransomware decryptors in the past, and now, EclecticIQ joins the mix with one of its own.
Ransomware is taking over the world, with multiple groups performing such tactics to infiltrate all kinds of victims. However, cybersecurity firms have bested them multiple times in the past, and this time, it’s no different.
It all began with a flaw in the encryption, which led EclecticIQ to concoct the decryptor. How did they pull it off? How can you use the tool? Find out below.
Free Key Ransomware Begets a Free Decryptor
Let’s face it. Ransomware is evolving in ways that not everyone can comprehend. Every now and then, threat actors are creating new variants and versions that pose new challenges for individuals, companies, and, of course, security firms.
Entities all over the world have fallen victim to such types of attacks, costing millions in the process just to retrieve their data.
However, as these threats are increasing, so is the cybersecurity firms’ determination to stop them in their tracks.
As we mentioned, Avast initiated the war against ransomware by creating a decryptor for the Hades variant. But the company didn’t stop there.
It also created effective decryptors for BianLian and Akira. Not to mention that BitDefender created one of its own, rendering MortalKombat ransomware useless.
Now, EclecticIQ is pitching in with its own decryptor that helps “Free Key” Ransomware victims retrieve their files for free.
The group was seen on darknet markets, offering stolen data and SIM cards, as well as other harvested information. A sample of their ransomware notes is presented below:
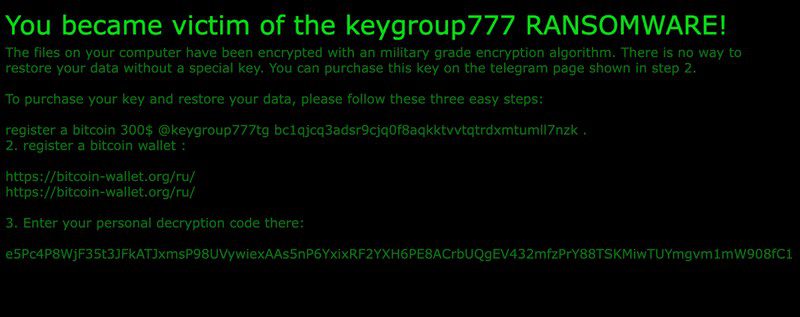
Well, it doesn’t seem to be “No way” to restore the encrypted data, thanks to EclecticIQ. Of course, just like all the aforementioned decryptors, this one only works on specific variants. You know, cybercriminals will always pick up on this news and tweak their code.
The decryptor came after the researchers found a vulnerability in the encryption tool used by the attacks.
As a result, they were able to concoct it, stating that the group, which seems to be of Russian origin, is a “low-sophisticated threat actor.”
This particular decryptor comes in Python Script form, which users can save and run using the following command:
python decryptor.py /path/to/search/directory
Once run, the script will navigate the device for files with “.KEYGROUP777TG” extension and decrypt them. There you have it – that’s all you need to do.
A New Ransomware Variant Taken Down
Before decrypting your files, it’s highly recommended you create a backup for the encrypted ones. You never know what may happen during the decryption process.
Aside from that, the decryptor only targets variants released near August 3rd, 2023. If the group managed to upgrade it, a new tool might be needed.





