Operation Dream Job: Lazarus Group Sets Sight on Linux Users
When it comes to cybercrime, threat actors vary in terms of methods of execution and how they impact an industry. They have to make a name for themselves. While some still lurk in the shadows, others, like the Lazarus group, have been terrorizing companies and organizations around the world. And yes, they’re back with a new target – Linux Users.

This is a very dangerous attack involving a huge social engineering scheme. What makes it even more frightening is that Lazarus is expanding its arsenal, marking this the first time the group has used Linux Malware.
Code Name: Operation Dream Job, DeathNote, or NukeSped – Lazarus is not kidding around with this one. What is this cyberattack all about? How is Lazarus implementing everything? We’ll explain everything below.
Linux Users – Into the Lazarus Pit
In the comics, the Lazarus Pit represents life or revival, to be exact. However, the Lazarus group itself represents nothing that positive.
We have our fair share of articles reflecting incidents with Lazarus. It’s just that the group has been around for quite some time now, as it is one of the oldest active cybercriminals groups.
Also tracked as ZINC, this North Korean hacking group is pretty capable, especially when it comes to harvesting personal information and sensitive data for several beneficial outcomes.
Yes, this particular group has been involved in so many cyber attacks in the past, and it doesn’t seem to be stopping any time soon. We’ve seen it target victims using several methods, especially phishing attacks.
Whether it’s impersonating Lockheed Martin, BloxHolder, and Singapore-based cryptocurrency exchange firm Crypto[.]com.
This time around, Lazarus is shifting its ways as it’s targeting Linux users. As always, the threat actors are using social engineering techniques in the form of fake job offers to lure their victims.
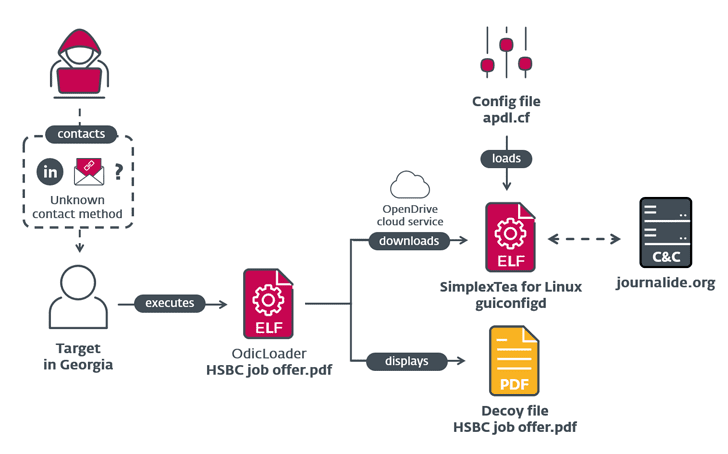
According to ESET’s report, the attack involves a fake HSBC job offer with a ZIP archive file containing a Linux backdoor named SimplexTea distributed via an OpenDrive cloud storage account.
The report doesn’t state how Lazarus is distributing the malware. In other words, the exact method used to distribute the ZIP file is still unknown.
However, we have to assume or suspect that they’re using spear phishing tactics or direct contact with the victims through LinkedIn.
The Lazarus Effect 4 – Linux Added to the Mix
Lazarus is a group that’s been terrorizing everyone all over the world. ESET states that this particular campaign has been prepared since December 2022. The threat actors are taking their time planning these malicious practices.
Throughout the years, Lazarus proved itself to be a force in the cybercrime world. Whether you’re a simple individual or a person who hosts a company, make sure that all the necessary precautions are in place.
You never know when you’ll become a target of Lazarus or any other cybercriminal group. Stay safe.





