Roaming Mantis Campaign Expands – Wroba Goes to Europe
Once again, threat actors are targetting Android and iOS devices with phishing attacks that distribute malicious apps and malware from outside the official stores. This time around, the main victims are users in Europe. And the attacker? The infamous Roaming Mantis.

The malware has been around for quite some time now but recently reached countries such as Germany and France. Usually, only Android users suffer from such campaigns. However, with this one, even iOS devices are at risk.
The infection method is different, but the results are the same – a trojan named “Wroba” that steals e-banking credentials. How global is this Roaming Mantis campaign and how do attackers implement it? We’ve covered everything in this article.
An Infectious Mantis Bite – Wroba Spreads Quickly
Spreading malware through SMS messages has become a popular practice among cybercriminals in the past few years. Mainly, their main target is Android due to its OS’ lack of security.
The new Roaming Mantis campaign is not going by the books as it’s attacking both Android and iOS devices, sparing no one in European countries.
Roaming Mantis uses Smishing (SMS phishing) about a shipped package with an included URL for the users to click on.
The method the campaign uses is different on each OS. In fact, the received message might be the same, but the outcome differs based on the device.
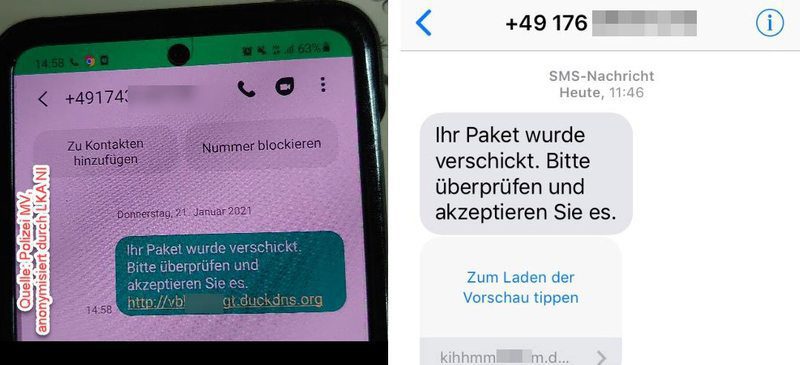
When it comes to Android, clicking on a link takes users to a page that asks the users to download certain apps as APK files from outside Google Play Store.
As reported by Kaspersky, the fake apps with the Wroba malware are more likely created for Google Chrome, but also may impersonate Yamato transport and ePOST apps.
However, iOS’ version is quite different. Due to the OS’ way of operation, users cannot download files from external sources for security reasons.
Now, if the victims click the link on an iOS device, they’ll head to a phishing page, where the attackers will attempt to harvest the user’s Apple ID login credentials.
Such smashing attacks are on the rise. In fact, Roaming Mantis has been doing this for over 3 years now. Back in 2018, it was targeting Android phones in Japan via DNS hacking.
Fast forward to 2022, the campaign has evolved in so many ways, tricking users into downloading tens of thousands of malicious APK downloads in Europe:
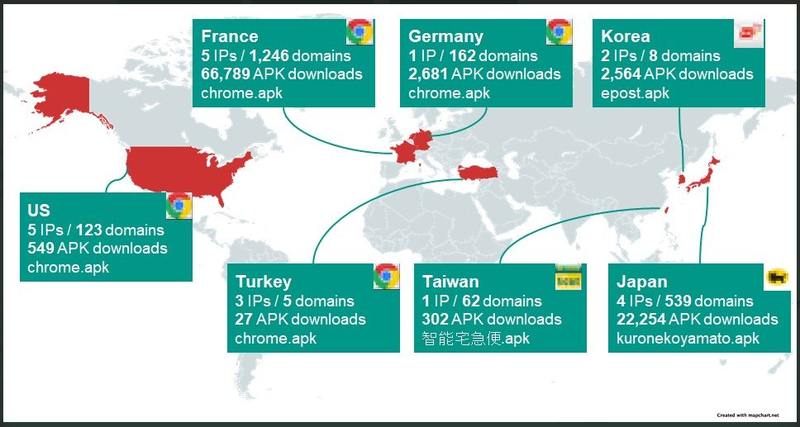
As seen in the image above, most users that have downloaded those malicious APKs reside in France. The Roaming Mantis is expanding, and according to what we’ve seen so far, it doesn’t appear to be stopping anytime soon.
The malware can also steal your images and perform several other commands that help attackers commit blackmail, fraud, identity theft, and extortion if sensitive media is stolen.
The Roaming Mantis: A Serious Bug Infestation
As mentioned, phishing campaigns are almost everywhere and you have to protect your private information no matter what.
A little reminder to all Android users: only download apps from the Google Play Store, and use an antivirus. iOS users, on the other hand, should never click on links that seem to be shady.
Never believe anything sent to you with an included link. If you’re waiting for a certain package, visit the source’s official page manually.
A few extra seconds will save you a lot of damage in return. Please note that these precautions will not protect you from all threats, but they will at least help you avoid this kind of Smishing predicament.





