SharkBot Malware: A Google Play Antivirus App Spreading a Dangerous Banking Trojan
Android OS is probably the most popular/used system around the world. It allows the user to do almost everything without applying any restrictions. Unfortunately, hackers and threat actors have the same privileges.

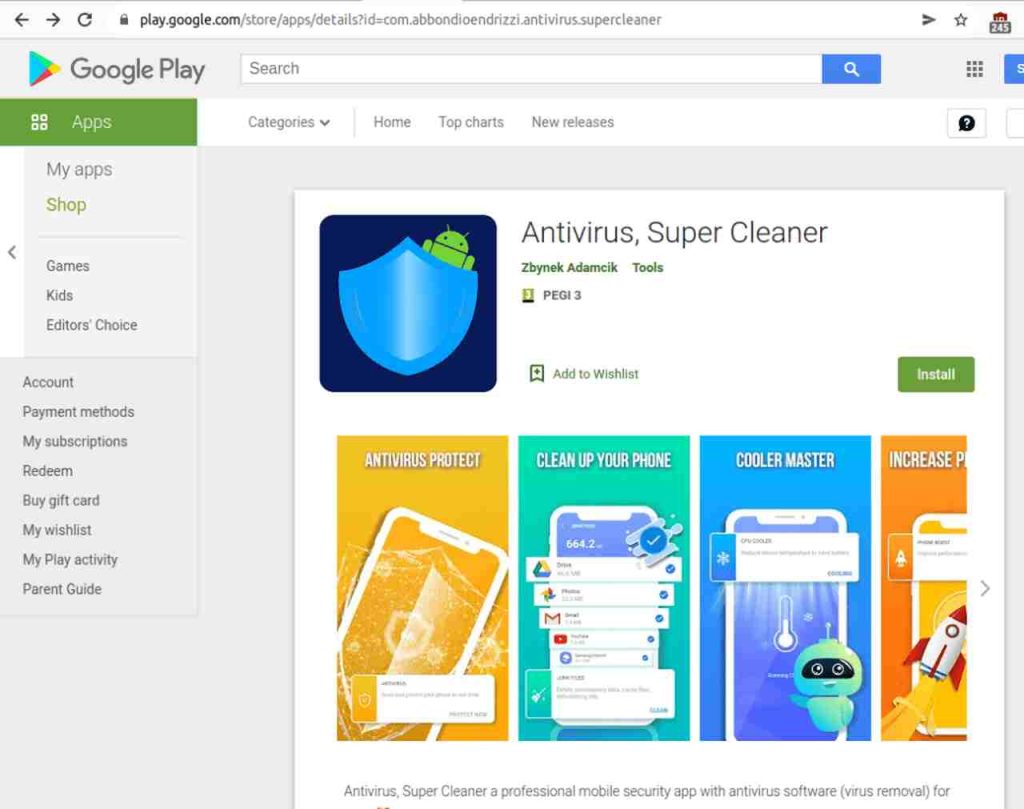
Android devices are well-known to be the main targets for cybercriminals as it’s easy to infiltrate. There have been previous incidents where Google Play hosted malicious applications. And now, a new trojan is found to be lurking within the store in the form of the Antivirus app – Antivirus, Super Cleaner.
The app hosts none other than the SharkBot banking malware and the outcome can’t be more serious. This definitely shows us that malware distributors can still bypass Google’s defenses and target millions of victims around the world. What is this all about? We’ll shed more light on the matter next.
SharkBot Malware is Lurking – Google Play Infiltrated Again
As we mentioned, this is not the first time threat actors were able to get around Google Play’s security measurements. However, with this particular attack, SharkBot seems to be using relatively new components unbeknownst to other trojans.
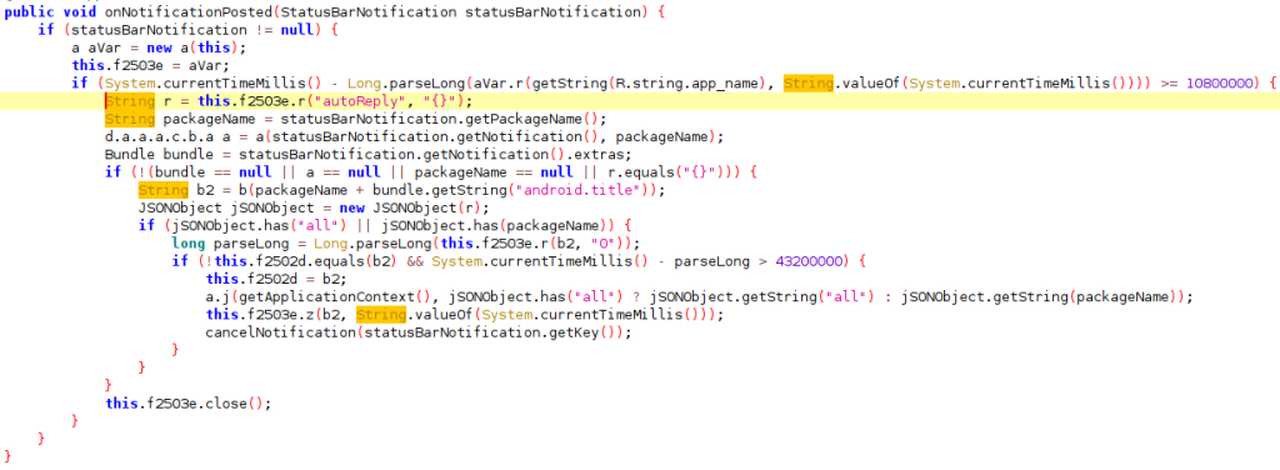
Apparently, SharkBot distributors are using the ‘Direct reply’ feature for notifications. Apparently, this has been used recently by FluBot, and now, SharkBot is taking the lead with it.
According to researchers at NCC Group:
“With this feature, the C2 can provide as message to the malware which will be used to automatically reply the incoming notifications received in the infected device.
In the following image we can see the code of SharkBot used to intercept new notifications and automatically reply them with the received message from the C2.”
Unfortunately, it doesn’t end here. We showcased how threat actors can distribute SharkBot, but we still have to talk about what it does.
In order to steal banking credentials, SharkBot uses these four main strategies: (Source: NCC Group)
- Injections (overlay attack): SharkBot can steal credentials by showing a WebView with a fake log in website (phishing) as soon as it detects the official banking app has been opened.
- Keylogging: Sharkbot can steal credentials by logging accessibility events (related to text fields changes and buttons clicked) and sending these logs to the command and control server (C2).
- SMS intercept: Sharkbot has the ability to intercept/hide SMS messages.
- Remote control/ATS: Sharkbot has the ability to obtain full remote control of an Android device (via Accessibility Services).
Apparently, the victim needs to enable Accessibility Permissions & Services. Once they do, SharkBot will be able to take full control.
It can intercept all the accessibility events when the victim interacts with the device utilizing the User Interface. That includes button presses, touches, TextField changes, and more.
More than 1,000 users have downloaded the app. Not to mention that the threat actors have been updating it, which means it has been there for a while.
NCC Group reported that the malware can initiate money transfers (from compromised devices) via Automatic Transfer Systems (ATS). This poses a huge threat to Android users.
A JAW-Dropping Discovery: A Store Full of SharkBots
The SharkBot malware can do a lot of damage once it infiltrates your systems. It can easily auto-fill fields in legitimate mobile banking apps and initiate money transfers.
There’s a lot to point out here in terms of keeping you safe. Even if Google Play Store hosts it, never blindly trust an app.
You can find a lot of popular Antivirus apps within your Store. Just try to keep installed apps on your device at a minimum. Stay safe.