SMSFactory Malware – Premium Services Activated… Without Your Consent!
Lately, Android seems to be hogging the spotlight when it comes to malware infection. A couple of days ago, Google Play was found to contain over 600 apps with banking trojans. Now, Android users are up against a new threat in the form of SMSFactory.

This campaign focuses on subscribing victims to premium services. This is definitely not new as we’ve seen several attacks of the sort in the past, including the one with Dark Herring.
SMSFactory has several sources to reach a victim’s device. Once in, the target is expected to receive unwanted costs to the phone bill. What is SMSFactory? How does this campaign operate? We’ve discussed everything in the following article.
SMSFactory – Premium Services You Never Wanted
SMSFactory’s operations are not as new as people might think. We’ve seen this before. However, the impact it has done is something to worry about.
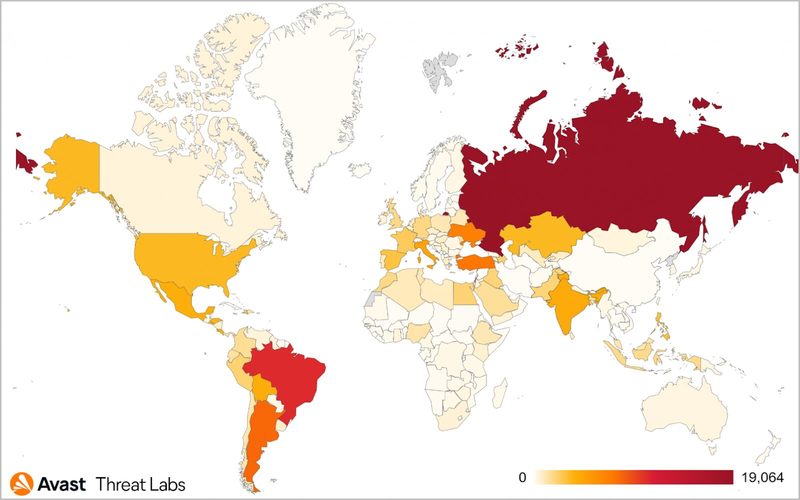
The malware was discovered by none other than cybersecurity giant Avast. Apparently, SMSFactory targeted tens of thousands of Android devices protected by Avast security products in several countries.
We’re talking at least 8, which is not a small number, considering the malware infected over 165,000 devices. According to Avast’s research, the most affected country is Russia, followed by several countries like Brazil, Argentina, Turkey, and Ukraine as seen in the map below:
So the question is: How are the threat actors behind SMSFactory distributing the malware? Again, nothing new here as they’re using the cliche techniques to target their victims.
To spread the malware across as many devices as possible, the attackers use methods such as push notifications, promo pop-ups, and malvertising.
However, with this particular campaign, the attackers are also including videos with promising video hacks as well as adult content access.
The Infection Process
As mentioned, the campaign reaches the victims using the methods above. Once received, it takes only a few clicks from the user to complete the process.
Despite having several sources to distribute the malware, everything ends up at a couple of places – unofficial app stores.
According to ESET researchers, both APKMods and PaidAPKFree are hosting the malicious APK package. Unfortunately, these Android repositories are quite famous, which ensures wide distribution.
#ESETresearch discovered that the #SMSFactory Android trojan found by AVAST is being distributed via 2 malicious Android app stores. Apps from these stores download the malware instead of the user intended app.
— ESET research (@ESETresearch) June 3, 2022
AVAST blog on the #SMSFactory malware:https://t.co/lrNwRYBqvA 1/2 pic.twitter.com/YsvS9RPXwE
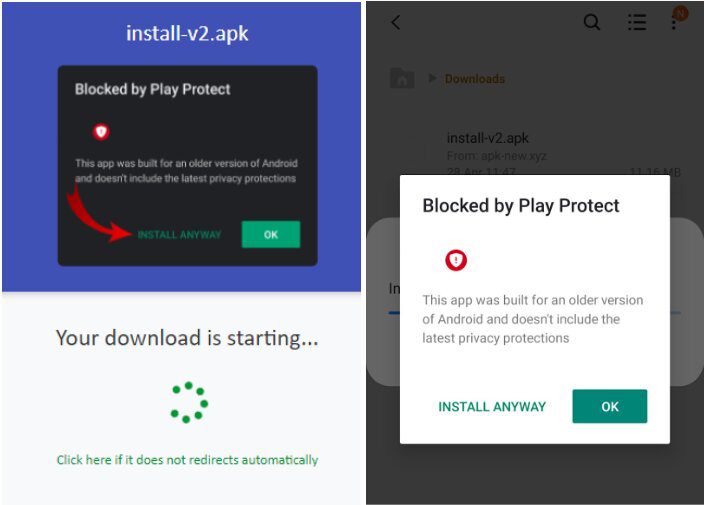
Installing the infected application won’t come without a warning. In other words, victims will still have a chance to avoid this entire predicament. But when a non-tech-savvy user receives it, he/she might ignore it knowingly.
When the file installation process starts, a warning pops up from Play Protect. Well, that’s the least we can expect from Android’s built-in security system as its main job is to alert users about the potential security risks from unknown files.
Aside from this warning, the type of permissions required by the app should be a clear sign of malicious activity. Once installed, the malicious application will ask the users to allow it access to SMS, wake/lock/vibrate, use the entire screen, start activities from the background, location info, manage overlay, and most importantly, make calls and send SMS.
When the app sets root, it’ll show up in a very weird way that no one would’ve expected. First, it presents the victim with a fake screen full of services that don’t work or are unavailable, to begin with.![]()
Second, the app does exist in the “Apps” section, but with no assigned name or icon. This makes it more difficult for the user to remove it. The app might be invisible, but SMSFactory is definitely doing its malicious job in the background, sending an ID profile of the infected device to the attacker’s command and control (C2) server.
SMSFactory Malware – Why Subscribe? They’ll Do it For You
In this campaign, the attackers keep a keen eye on the device to determine if it’s usable. If they do, they will start their malicious activity and subscribe the victim to premium services.
We did mention that allowing permission to “Calls and SMS” is very dangerous. This is due to the fact that different variants of SMSFactory can add admin accounts on the device and use text messages to further distribute the malware using the contact list.
To protect yourself, never download anything from unofficial sources. This goes specifically for apps that are supposed to be premium, as you’ll be paying for them in another way. Watch out and always stay vigilant.





