Trezor Phishing Campaign 2 – The “Sense of Urgency” Technique Revisited
Cybercriminals have resorted to phishing campaigns to execute their malicious practices for quite some time now. There are various forms of such attacks, with each one having its own effectiveness. Preying on a victim’s fear factor promises higher success rates, and that’s exactly what’s happening now with Trezor customers.

A huge campaign targets Trezor users with a scam where the sense of urgency plays a huge role. We had seen the same kind of attack a year ago. The goal is clear – steal a target’s cryptocurrency wallet and its assets.
Isn’t that what every cybercriminal is after when they target cryptocurrency operators? But the question is: How are they doing it? We’ll answer that in the following article.
Trezor Phishing Campaign – Your Assets Might Be At Risk
Cryptocurrency companies have been constant targets for cybercriminals in recent times. They are, indeed, a beneficial victim to harvest from.
In the past few months, the crypto industry has seen multiple malicious campaigns, including ones that involve dangerous groups such as Lazarus.
Unfortunately, this particular group seemed to be hell-bent on targeting crypto wallets no matter what the method is. Another attempt by Lazarus sees fake applications everywhere – talk about phishing attacks at their best.
When users operate crypto applications, targeting them by inducing fear is a pretty easy task. Threat actors are well aware of that, which leads to phishing campaigns with a “Sense of urgency” lure.
Recently, Trezor users have been receiving notices via SMS and email stating that Trezor had suffered a data breach.
A lot of individuals received such texts, including a security researcher known as Mich, which is shared on Twitter as seen below:
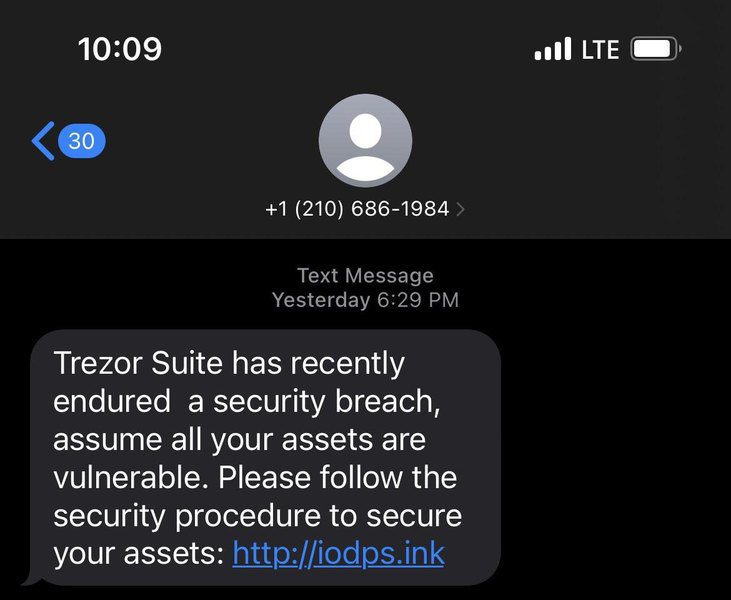
When the recipient clicks on the link provided in the SMS/Email, it’ll redirect him/her to a fake page, where the campaign proceeds with another lie.
This time, they’ll be on a fake Trezor site that includes a warning: “Your assets might be at risk!” A “Start” button is also there to click on as the page prompts you to start securing your wallet.
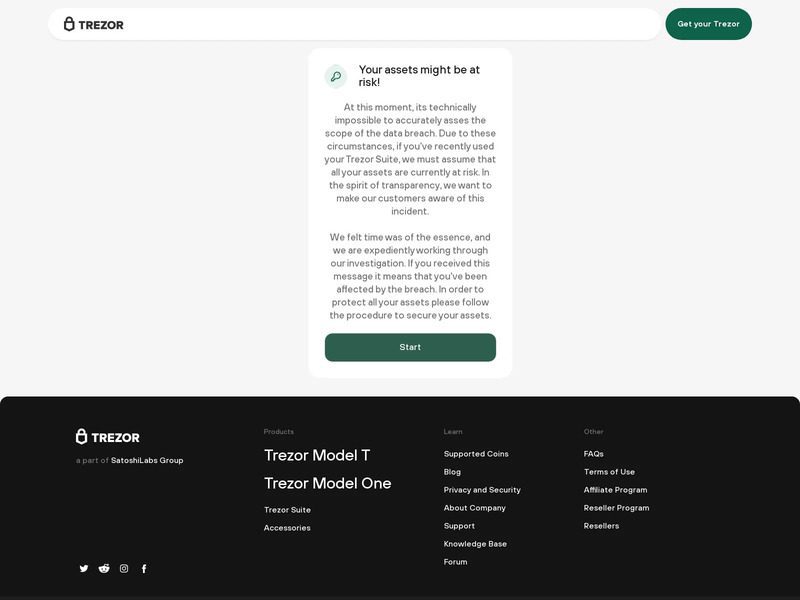
Here’s where the malicious magic happens. When users are setting up a Trezor wallet (The Real One), they are provided with a 12 or 24-word recovery seed, which they can use to recover their wallet in case their device was lost.
We had to explain that because it’s actually what the cybercriminals are looking for in this campaign. Clicking on the “Start” button will open a Window that prompts the users to enter their recovery seed, which the threat actors will then harvest.
With the seed in their possession, the threat actors can immediately transfer any assets to another address they own – and game over.
Apparently, Trezor is well aware of the phishing campaign and released a statement to inform its customers:
“Beware of the active phishing scam! The attackers contact the victims via phone call, SMS and/or email to say that there’s been a security breach or suspicious activity on their Trezor account.
Please ignore these messages as they are not from Trezor. We have not found any evidence of a recent database breach. We will never contact you via calls or SMS.”
We don’t know who is behind the attack and how they got their hands on the customers’ emails. However, we can rule anything out, especially as it could be through the marketing list harvested in a MailChimp breach.
The Crypto Industry is Under Attack
As we mentioned in the introduction, this is not the first time Trezor was used in a phishing attack. The platform has many users that would easily fall victim to the right lure.
Whenever you receive an SMS or an email with a link inside, the first thing you should do is act as if it’s a threat actor all the time.
Stay vigilant and click no link. That way, you’ll save yourself a lot of trouble – it’s your private information at risk. Protect it.





