New Windows Phishing Campaign: A Malware Triple Threat
Phishing campaigns have increased drastically in 2022, reaching new heights as cybercriminals are coming up with new ways to infiltrate your devices. Normally, a phishing campaign’s main aim is to infect systems with malware. If one single malware can cause unspeakable damage, what can three at a time do?
Unfortunately, that’s the case we’ll be talking about today as a new campaign is on the rise, involving the injection of three malware trojans: AveMariaRAT, BitRAT, and PandoraHVNC.
The campaign does include three different malware trojans, but their job is pretty common: They’re all designed to steal sensitive information from victims. So, what is this campaign about? How are threat actors targeting their victims? Find out in this comprehensive article.
New Windows Phishing Campaign – x3 The Damage
As we mentioned, phishing campaigns using fake emails have become a popular method to infiltrate systems, regardless of the region. Not long ago, targets were receiving phishing scams sent by big companies such as Lockheed Martin and WhatsApp.
These two attacks made a huge impact, especially the WhatsApp one, considering the number of users the social media platform has. Now, threat actors are kicking it up a notch with a new attack, using multiple malware trojans for better results.
The campaign is quite obvious in terms of the outcome. With three different forms of malware, cybercriminals are aiming to steal usernames, passwords, and other sensitive information, including bank details. According to Fortinet’s FortiGuard Labs, these are the exact details that best describe the campaign:
- Affected platforms: Microsoft Windows
- Impacted parties: Microsoft Windows Users
- Impact: Controls victim’s device and collects sensitive information
- Severity level: Critical
So how does this happen? The whole process kicks off with an email disguised as a notification of a payment report from a trusted source.
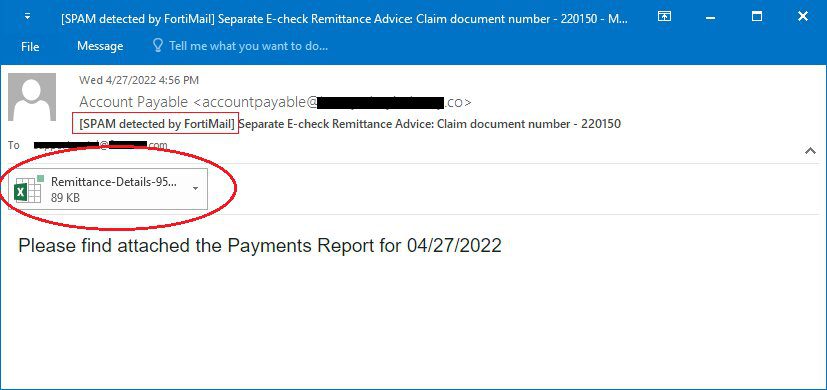
Just like most phishing campaigns, the email is a way to trick the recipient into opening the attached Excel document for the report detail.
Once it’s clicked on and opened, Microsoft Excel presents the user with a warning. That alone should be a sign not to continue.
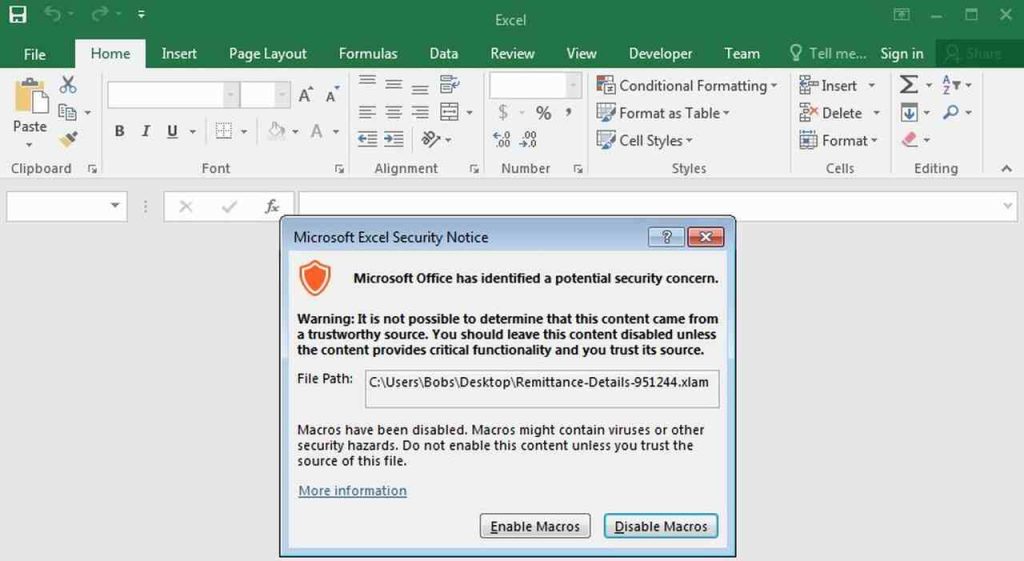
Normally, when this happens, the file must be closed immediately. However, if the user doesn’t know his way around, they’ll proceed.
The (*.xlam) file contains malicious macros, and once the user enables them, it starts the process of delivering malware. The threat actors use Visual Basic Application (VBA) scripts and PowerShell to retrieve the malware and install it on the target’s Windows device.
In the end, it splits the PowerShell code into three parts as there are three different forms of malware. FortiGuard didn’t state why three malware payloads are being used.
However, with a saying such as “The More The Merrier” in mind, it’s quite obvious that the threat actors are looking for a greater chance to gain access to whatever sensitive information they’re looking to steal.
Windows Phishing Campaign – Three Times the Alarm
We’ve seen many phishing attacks before, but using three different forms of malware, it’s quite the upgrade for threat actors.
AveMariaRAT, BitRAT, and PandoraHVNC are three different, but equally dangerous payloads. All we have to say is that whenever you receive such emails, always be vigilant.
Not only that, but always heed the warnings, never ignore them. Your sensitive data is on the line, this is not something you can put at risk.





