Ermac 2.0 Hits Android – Polish Foodies Beware
When it comes to Android, there’s no guarantee what kind of malware attack is on the rise. A while ago, over 200 Google Play apps were found to be distributing the Facestealer malware. Now, a new campaign targeting Android is in place, using none other than ERMAC. Well, version 2.0.

If you think food apps are convenient, then what we’re going to discuss is going to make you lose your appetite. The malware is spreading through a fake Bolt Food application within the Polish market.
All it takes to complete the injection process is a few clicks and a couple of permissions. As a result, the threat actors will be able to easily steal account credentials and crypto-wallets. What is ERMAC 2.0? How is it utilized by hackers? Make sure you give this article a quick read.
Ermac 2.0 – Very Costly, Very Effective
Imploying malware on Android devices is not a new trend. In fact, the platform has been targeted a lot lately, mainly due to the fact that its security allows third-party downloads.
While downloading applications from Google Play Store isn’t that safe just like previous incidents showed, getting your software from unofficial sources is totally dangerous.
You never know who’s hosting the site or what malware is embedded within the downloadable file. This case is proven with the Ermac malware.
Apparently, threat actors are sending fake ads impersonating the legitimate European food delivery service – Food Bolt. The ads are spread through phishing emails, malicious social media posts, smishing, malvertising, and more.
Once you click on the provided link in the aforementioned sources, you’ll be redirected to a fake website that looks like the official Food Bolt domain.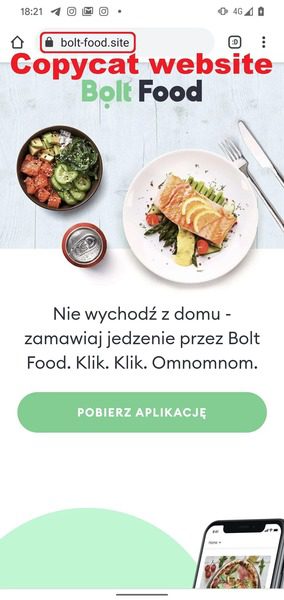
Before we proceed, we have to, unfortunately, notify our readers that this site is still up and running. Now, as seen in the image above, there’s a huge button.
This downloads the application on the device. Once the victim completes this task, a permission request pops up, demanding complete control of their device.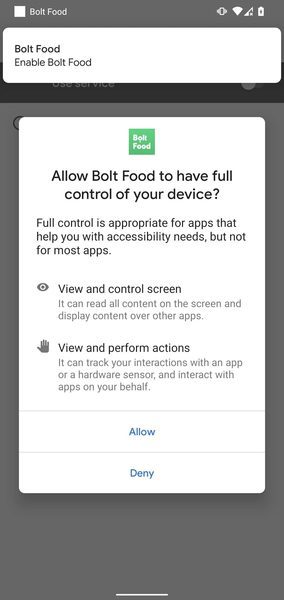
Users who are not tech-savvy can easily fall victims to such a trick. They will grant permission to Accessibility Service without even knowing what they’re jeopardizing.
Consequently, they’ll enter their credentials on forms that look legitimate but are just fake identical ones of the actual application interfaces.
Command & Conquer? More Like Conquer & Command
According to researchers at Cyble, once the user clicks accept, he/she will be granting the fake app around 43 permissions. This includes system alert window creation, SMS access, contact access, audio recording, and full storage read/write access.
Aside from that, the Ermac malware is capable of performing the following commands:
- registration – Sends device data
- updateBotParams – Sends the updated bot parameters
- downloadInjection – Used to receive the phishing HTML page
- downloadingInjections – Sends the application list to download injections
- logs – Sends injection logs to the server
- checkAP – Check the application status and send it to the server
The researchers at Cyble found this malware to be similar to a previous one that targeted several operating systems in the past.
They compared it to the “Cerberus” malware. Apparently, threat actors took inspiration from this malware to create the new powerful Ermac 2.0 trojan.
In case you didn’t know, threat actors are selling the malware on the darkest of dark websites for around $5000. It’s much more expensive than its predecessor, but in the end, it’s capable of so much more.
Ermac Reinvented – Chaos in the Android World
The fact that this malware can reach dozens of different applications is scary. It can identify what apps the user has on his device and inject similar fake pop-ups to lure him in.
We always advise our readers to stay vigilant when they download files, especially when it’s not an official source. Google Play Store might have some security flaws, but it’s safer than third-party websites.
Read the reviews, and check the ratings – this can save you a lot of trouble now and in the future. Stay safe.





