Octo Hits Android – A New Banking Malware on the Rise
Android devices are the most popular platforms in the world nowadays. However, with popularity comes a lack of security, which makes the devices the main targets for cybercriminals. A while ago, Android suffered a hit by Sharkbot malware distributed through Google Play. Now, the banking malware Octo is on the rise.

The fact that any Android users can tinker with the operating system of their phones and tablets makes them more susceptible to cyberattacks. Not only that, but it also attracts cybercriminals as you can download anything on the device.
This time around, several fake apps are spreading the Octo banking malware, be it on Google Play Store or a third-party source. It’s big, it’s dangerous, and we’re here to shed more light on the matter.
The Octo Android Malware – A Malicious Sticky Situation
As mentioned, the Octo malware was spreading through various means targeting Android devices. Users are downloading the malware from fake pages and even Google Play Store.
This is not the first time that Google Play hosted malicious applications. Now, the Octo malware is taking over, featuring remote access capabilities such as on-device fraud.
A couple of years ago, Android devices witnessed the rise of the Exo trojan. However, the malware ceased to exist in 2018 and got its source code leaked later that year.
Apparently, cybercriminals got fond of the malware and recreated an elevated version of it in the form of Octo. Basing the new malware on ExoCompact, the rebranded Octo malware can do a lot of malicious deeds, especially remotely controlling the compromised Android device.
Once Octo takes root in the victims’ devices, it allows the threat actors to perform all sorts of malicious practices. Unfortunately, the malware does those actions without the victim’s knowledge.
How? Well, it blackens the screen by setting the brightness to 0. After that, it disables all notifications so that the device appears to be turned off.
Now that the victim is in the dark, the threat actor can write texts, modify the clipboard, copy/paste data, tap on the screen, as well as scroll up and down. This is what On-Device Fraud looks like:
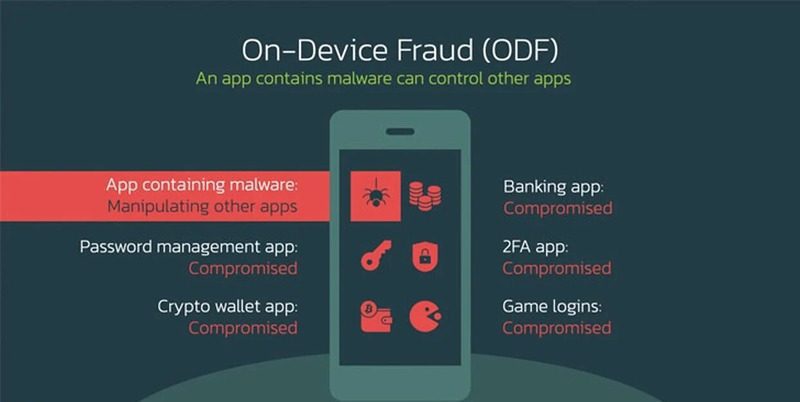
As we presented in the image above, we can easily say that this malware is very dangerous. It compromises a lot, which may result in drastic consequences.
Octo Has Wrapped Its Tentacles
The remote access system is quite the risk, but unfortunately, there’s more. We did state that this new version has elevated features, and we weren’t kidding.
Octo doesn’t only perform RAS, but can also monitor and record every single action a victim performs on his/her device. We’re talking about clicks, websites, PINs, and a lot more.
Apart from the remote access system, Octo also features a powerful keylogger that can monitor and capture all victims’ actions on infected Android devices.
Aside from that, Octo can also apply the following commands:
- Block push notifications from specified applications.
- Enable SMS interception.
- Disable sound and temporarily lock the device’s screen.
- Launch a specified application.
- Start/stop remote access session.
- Update list of C2s.
- Open specified URL.
- Send SMS with specified text to a specified phone number.
According to Threat Fabric, anyone could find the malware Octo on forums, such as the Russian-speaking XSS hacking forum. The author goes by the alias “Architect” or “good luck.”
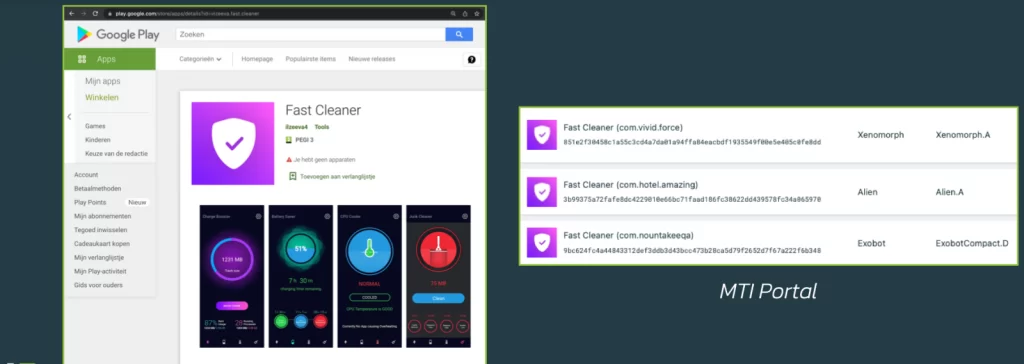
Now, how do victims get Octo on their devices? With it being available for everyone, the ways are almost infinite. Recent Google Play apps have shown to have Octo embedded within them.
For example, an application called “Fast Cleaner” had more than 50,000 installs until February 2022. It’s now removed by the official Store.
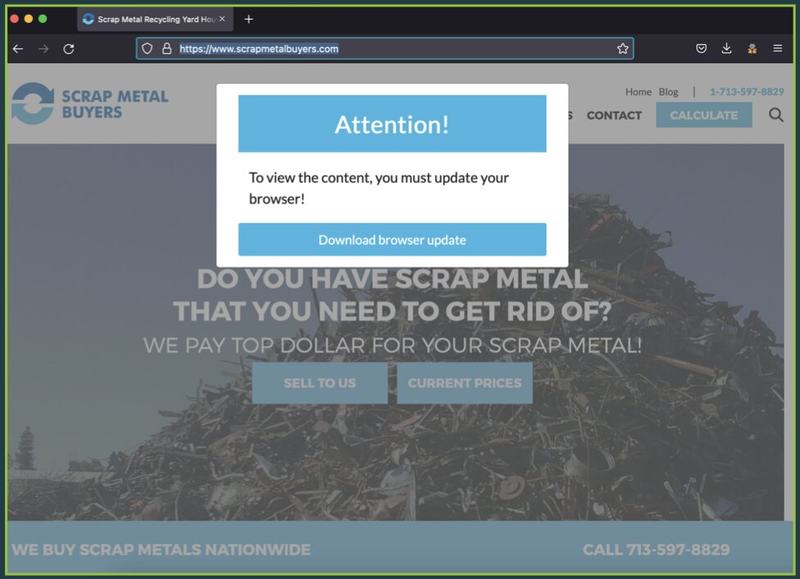
We did mention that Google Play Store isn’t the only source where the campaign is being spread. The Octo malware is also available through fake websites prompting users to either update their browsers or applications through the Play Store.
Banking malware is getting stronger and stronger as technology advances. Always make sure that the app your download is legit. You can do so by checking the comments of previous users.
One Malware – Seven Tentacles (Apps)
Thanks to Threat Fabric’s report, we were able to get the full list of the infected applications:
- Pocket Screencaster (com.moh.screen)
- Fast Cleaner 2021 (vizeeva.fast.cleaner)
- Play Store (com.restthe71)
- Postbank Security (com.carbuildz)
- Pocket Screencaster (com.cutthousandjs)
- BAWAG PSK Security (com.frontwonder2), and
- Play Store app install (com.theseeye5)
Now, the apps that were available on Google Play Store have been removed. As you can see, even Google Play Store cannot be trusted all the time.
Octo Android Malware – Download, Infect, Constrict
While you must trust Google Play with the apps it hosts, your task is to stay vigilant all the time. Never download software from third-party sources that you’re unsure of.
Also, if you have installed any of the apps, we recommend you remove them now. Once you’re done, perform a quick virus check using reputable anti-virus software.
Don’t take your device’s security lightly. Cybercriminals are always coming up with new ways to steal your data. When one malware dies, another comes out with elevated source code. Make sure you’re aware of that and you have all the means to protect yourself. Staf safe.




