Facestealer Malware Found in Over 200 Google Play Apps – Your Privacy is At Risk
Android is by far and without a doubt the most popular operating system in the world. Thanks to its Play Store, users get to download millions of applications and programs with complete ease. It’s just the safest place to get apps from. Or is it?

Unfortunately, Android devices are known to be very vulnerable to attacks, especially malware injections embedded within downloaded applications. While most of these campaigns come from external downloads, Google Play also falls short on security at times.
The Android App Store did slip up in the past as it hosted several apps containing Octo and Sharkbot malware. Now, Google Play remade the mistake yet again.
But this time, over 200 malicious apps are spreading the spyware called Facestealer to siphon user credentials and other valuable information. What apps are infected? How does Facestealer operate? Find out in the following article.
The Facestealer Malware – Google Play Did It Again
The malware injection on Android has become a very popular technique among cybercriminals in 2022. In fact, statistics show that more than 11,000 new Android malicious apps are being launched on the market each day, and most of them are adware.
As mentioned, Android users are always at risk when it comes to downloading applications. The device itself is safe, but the downloading practice is definitely not, especially when the source is not credible.
Unfortunately, these users appear to be unsafe even if they’re using Google Play Store to get their desired applications. Most apps that belong to categories such as fitness, photo editing, and puzzle are always fun.
That’s why they pose as a huge attraction to a lot of users. Well, it’s sad to say that their popularity also reaches the cybercriminals’ radar.
According to a report by Trend Micro analysts, more than 200 Android apps are masquerading as tools that fall into the aforementioned categories to inject the Facestealer malware into the victims’ devices.
“Similar to Joker, another piece of mobile malware, Facestealer changes its code frequently, thus spawning many variants. Since its discovery, the spyware has continuously beleaguered Google Play.”
Apparently, the malware has one goal – plundering sensitive data. Aside from that, the applications can also collect Facebook cookies and personally identifiable information associated with a victim’s account.
Facestealer – The Malicious Apps
200 is a very big number, especially due to the fact that they’re all hosted on Google Play Store. How did these applications manage to bypass Google’s security?
The apps vary in terms of category. 42 are VPN services, followed by a camera (20) and photo editing applications (13). Not only that, but researchers found 40 rogue cryptocurrency miner apps that target users interested in virtual coins.
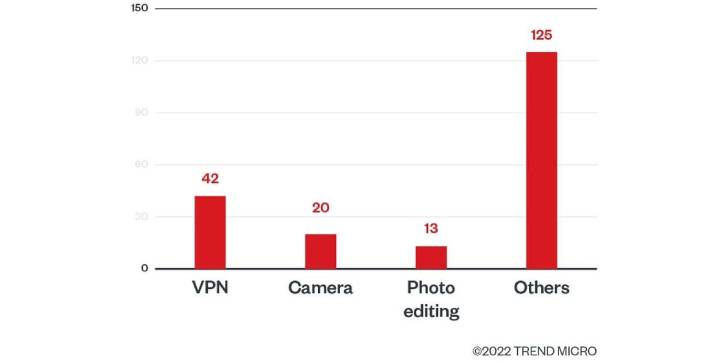
Once the victim uses those applications, they inject malware designed to trick them into watching ads and paying for subscription services.
There’s an app called Farm Your own Coin and similar ones to it that can do so much more than that. They can harvest private keys and mnemonic phrases that are used to recover access to a cryptocurrency wallet.
Having these apps on Google Play is quite dangerous. Unfortunately, no user is safe as everyone who operates an Android considers the app store as the most trustworthy source of download. Be careful when choosing an app.
Facestealer – More Like Everything-Stealer
Apps that inject malware have become very popular among cybercriminals. There’s not much you can do if Google Play Store can’t control such campaigns.
However, what you can do is be vigilant all the time when downloading an app. We recommend checking negative reviews so that you’ll know what previous users have experienced.
Other than that, small research won’t hurt anyone. That way, you can verify the legitimacy of the developers, and as a result, avoid this whole predicament.





