CapCut Impersonated: From Video Editor to Malware Injector
In the world of cybersecurity, popularity is both a blessing and a curse, especially if the thing in question is an application. Threat actors prey on these apps, creating fake clones to inject malware into their victims’ devices. This is exactly the case recently as a new campaign is masquerading as the CapCut video-editor service.

With over 500 million downloads on Google Play alone, CapCut has harnessed enough popularity to be known all over the globe. However, in some countries like Taiwan and India, the service is banned, which makes tricking residents there easier.
By creating a fake website, threat actors managed to trick those seeking alternative ways of downloading the program. Unfortunately, all they’re getting is an info-stealer. Which one exactly? How are the cybercriminals pulling this off? Find out below.
CapCut Clone: One Clone, Two Info-Stealers
Creating fake websites to lure victims and prompt them to download bogus content has become a common practice among cyber criminals.
They rely on popularity, and when it comes to that, CapCut cannot get any more popular. As we mentioned, the application has more than 500 million downloads on Google Play Store alone.
However, its website also gets the recognition it deserves, as it receives over 30 million hits on a monthly basis.
Unfortunately, some countries don’t have that privilege courtesy of nationwide bans, forcing residents to search for alternative download methods.
This reflects the best time to strike, and strike they did. The threat actors behind the attack have launched two separate campaigns involving two info-stealers.
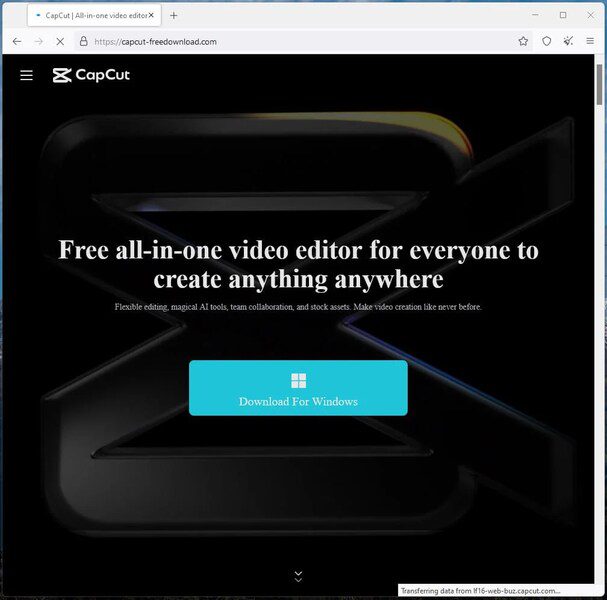
How the users end up on that website remains unknown. But according to Cyble, it should be via SEO, search ads, and social media.
Campaign #1
The first campaign sees a fake CapCut website with a Windows downloader button. Clicking that delivers a copy of the Offx Stealer on the user’s computer.
Since its binary is compiled on PyInstaller, it’ll only run on Windows 8, 10, and 11. Once the file is executed, a fake error message instantly appears, informing the launch has failed.
Well, we’ve been through a lot of similar campaigns to know that the Offx malware has started working in the background. This particular stealer is very capable.
It can harvest sensitive information such as cookies and passwords from (.txt, .lua, .pdf, .png, .jpg, .jpeg, .py, .cpp, and .db) file types, passwords, as well as cookies from web browsers.
Not only that, but it can also siphon data from messaging apps such as Telegram and Discord, as well as cryptocurrency wallets (Ethereum, Exodus, Atomic, Zcash, and more.)
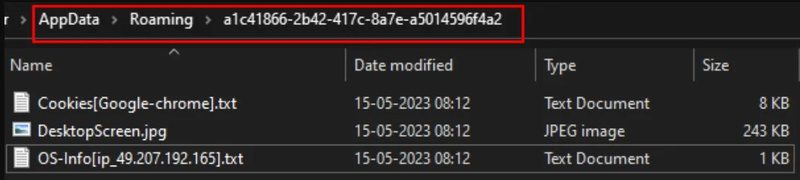
Once the malware collects the necessary data, it sends it to the operators on a private Telegram channel. When that’s out of the way, Offx deleted the local directory to wipe any traces of the infection.
Campaign #2
The second campaign involves one of the most known info-stealers across the globe – RedLine. We’ve written so many articles about incidents where RedLine is in the spotlight, and now, here it is again.
This one also begins with a fake CapCut site where the users are prompted to download a fake installer. When they click on the button, it’ll drop the file ‘CapCut_Pro_Edit_Video.rar’ on the victims’ devices.
The file contains a batch script that initiates a PowerShell script when opened. According to researchers at Cyble, the loader has over-the-top stealth capabilities that even antivirus engines could not flag the batch file as malicious.
When the PowerShell script is in place, it kicks off the final procedure, which is loading the final payload. Enter Redline Stealer and the .NET executable.
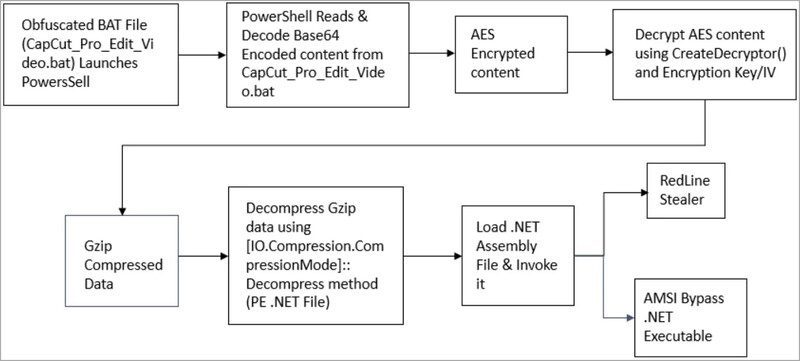
With RedLine lurking around inside the victims’ devices, threat actors can get a hold of sensitive information from web browsers and applications, including credit cards, usernames, passwords, and auto-complete data.
Stay Away from Untrusted Sources
Whenever you want to download a certain file, just do so from an official source. You won’t find websites providing your desired content all of a sudden without any official announcement.
If you receive a link via email or Telegram, ignore it. You never know who’s behind it and what plans they have for you once you click it. Stick to official sources and stay safe.





