Adware-Infected Apps with Over 3 Million Downloads Invade Google Play Store … Again!
Apparently, cybercriminals have made a habit of injecting adware into several applications on the Google Play Store. Not much time has passed since the last infiltration, and now, Android users are facing yet another malicious predicament – Autolycos malware in about 8 applications.

In Greek mythology, Hermes rewarded “Autolycus” with skills in trickery. That’s exactly what the malware does once it takes root within the device’s system.
The trick here is that Autolycos secretly subscribes users to premium services, which is a huge deal. However, what makes this worse is that the infected apps have millions of downloads.
Autolycos Malware – We’ll Subscribe on Your Behalf
Android users are always susceptible to cyber attacks as the device itself allows any kind of download, regardless of the source.
Every cybersecurity expert out there always recommends the use of the device’s official app store for downloads. However, even a giant like Google Play Store may have a misstep or two every now and then.
Google Play Store has had its fair share of malware infiltration in the past few months. A while ago, the Android store hosted over 200 applications that were spreading the infamous Facestealer malware.
Now, Google Play is, yet again, a target for cybercriminals as they embedded about 8 malicious applications within its library.
The applications have more than 3,000,000 downloads, which shows how big this incident is. With so many users operating these apps, the threat actors will generate millions through unnoticed premium subscriptions.
- Gif Emoji Keyboard (com.gif.emoji.keyboard) – 100,000 downloads
- Freeglow Camera 1.0.0 (com.glow.camera.open) – 5,000 downloads
- Wow Beauty Camera (com.wowbeauty.camera) – 100,000 downloads
- Vlog Star Video Editor (com.vlog.star.video.editor) – 1 million downloads
- Creative 3D Launcher (app.launcher.creative3d) – 1 million downloads
- Coco Camera v1.1 (com.toomore.cool.camera) –1,000 downloads
The six applications above were the first to be removed by Google Play. However, two more ramined a bit more, before being taken out as well.
These apps are ‘Funny Camera’ by KellyTech, which has over 500,000 installations, and ‘Razer Keyboard & Theme’ by rxcheldiolola, which has over 50,000 installs on Google Play.
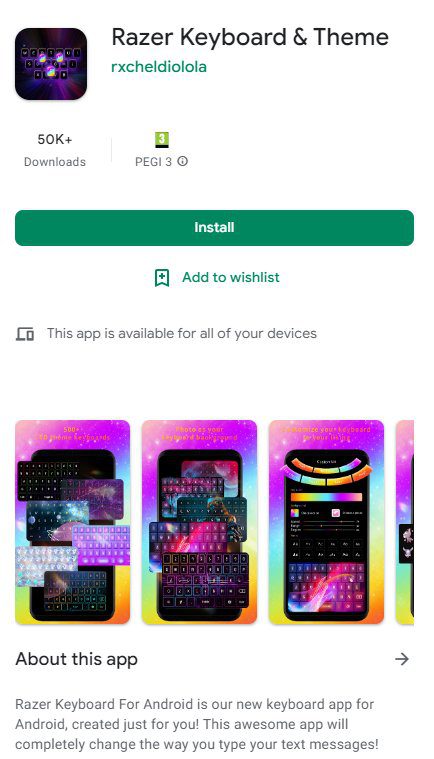
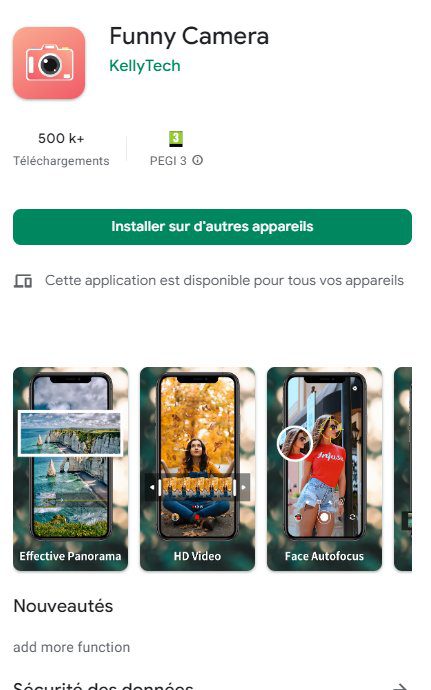
The malware works by executing advanced techniques to avoid detection, especially by the users operating the infected device.
And just like other apps that work in a similar way, Autolycos will request permission to access text messages. This can be a problem, especially if users regularly receive OTP passwords.
The Wide Spread
The threat actors behind the malware are using every method possible to spread out. One of these techniques involves numerous advertising campaigns on social media, especially through Facebook.
According to the study by Evina’s security researcher Maxime Ingrao, Facebook had about 74 ad campaigns for the Razer Keyboard & Theme alone.
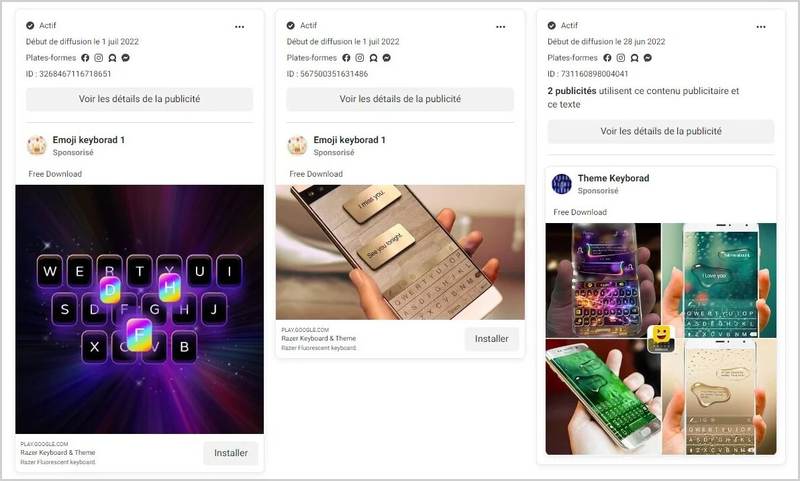
Most of these malicious applications had negative reviews on the Play Store as they did not deliver what they have promised. However, just like malware infiltration, hackers can also insert Bot reviews, which guaranteed millions of downloads for some of the apps.
Autolycos Malware – Background Premium Services Activated
We always recommend downloading applications from an official source such as Google Play Store. However, even if that’s the case, users should always check what reviews have to say. In other words, do a quick background check before downloading.
Moreover, they should always monitor if anything unusual is occurring on their device. We’re referring to data and battery consumption.
Finally, keep any security measures such as antivirus or Play Protect enabled. This will definitely minimize the chance of your device being infected. (P.S: All the applications have now been removed from Google Play)




