CircleCI Phishing Attack – Github Users Beware
Phishing attacks vary in the level of impact. Some are small, some are big, and then again, some are huge when the target is none other than Github. Such attacks are on the rise – threat actors even exploited the death of Queen Elizabeth to infiltrate their victims’ devices.

Now, a new phishing campaign is impersonating the CircleCI DevOps platform to steal users’ Github credentials and two-factor authentication (2FA).
With a fake “Session Expired” message, a lot of users will fall for the trick as it has a “sense of urgency” factor within it. How are they spreading the campaign? What’s on the line? Find out below.
Session Expired – Simple Notice, Huge Malicious Impact
CircleCI is used all over the world. The service kept evolving over time and made it more convenient for its users. It even announced a more generous free tier in 2022.
Ever since the launch, more than 58,000 organizations have signed up to CircleCI orbs in their CI/CD pipeline. In other words, any attack with the company’s name will have devastating effects.
Using big names in phishing campaigns is the easiest way to trick victims. It adds trust and legitimacy, which promises higher success rates.
The entire process starts with an email – shocker! The fraudulent messages include a notice that the users’ CircleCI sessions have expired.
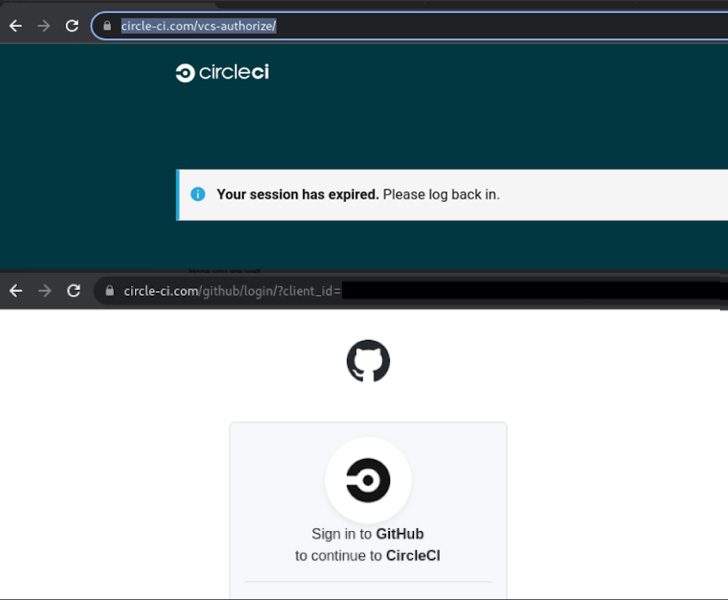
The victims are prompted to sign in using their GitHub credentials. How? Well, they have to click on the link within the email – a typical phishing practice.
However, it doesn’t stop here. According to CircleCI, the phishing campaign includes another form of email, which asks users to submit their credentials if they wish to accept the company’s new Terms of Use and Privacy Policy. Of course, they should also click on the provided link.
So, what does clicking on the link lead to? It allows unauthorized access to the user account. In other words, the threat actors can create GitHub personal access tokens (PATs), authorize OAuth applications, or add SSH keys to stay in control even if the user changes his/her password.
GitHub said it learned of the attack on September 16, 2022, adding the campaign impacted “many victim organizations.” It also stated that those who protect their accounts using hardware security keys are not vulnerable to this attack.
GitHub Users Beware – This CircleCI Phishing Attack is Real
Phishing attacks have been increasing ever since 2022 kicked off. Unforuntaltey, they don’t seem to be slowing down any time soon.
When it comes to phishing, clicking on the embedded link is the key to the attack’s success. All you have to do is avoid that by staying vigilant all the time.
Never trust an email that requires your personal information. If you want to know what’s going on, we highly recommend visiting the official website manually – don’t click on the link.





