Ducktail Malware Strikes – Facebook Business and Ad Accounts At Risk
Cybercriminals are expanding, and it’s pretty obvious. We’ve seen previous attacks on well-known companies, but apparently, they’re looking for diversity. In the past week, threat actors deemed educational institutions as targets. Now, individuals in managerial, digital marketing, digital media, and human resources roles in companies are under the Ducktail Infostealer Malware’s radar.

Apparently, the campaign is all about getting the victims to download some sort of payload, which allows the attacker to take over any Facebook Business account.
The targets have to be high-profile, which leads to full control of the Facebook Business account that the victim has access to. Who is behind this and what are they after? Find out below.
Ducktail Malware – Target Diversity at Its Best
We have to acknowledge this: Apparently, info-stealing malware is a trend nowadays among cybercriminals. In the past couple of months, such attacks have shown a great spike in numbers. First, there was the Amadey info-stealer, which targeted victims using the Smokeloader backdoor.
Now, Ducktail is in the spotlight with Facebook Business and Ad Accounts as its main goal. If these are breached, a lot of damage can be done to the owner.
This is definitely a financially driven cybercriminal operation, which according to Finnish cybersecurity company WithSecure’s (formerly F-Secure Business) report, contributes to a Vietnamese threat actor:
“The threat actor targets individuals and employees that may have access to a Facebook Business account with an information-stealer malware.
The malware is designed to steal browser cookies and take advantage of authenticated Facebook sessions to steal information from the victim’s Facebook account and ultimately hijack any Facebook Business account that the victim has sufficient access to.”
As we mentioned, the attackers have diversity when it comes to choosing targets. The cybersecurity company states that these threat actors have been operating since 2021. Particularly, in the latter half of the year.
Here’s how the process goes. The attackers trick the users into downloading supposed Facebook advertising information hosted on MediaFire, Apple iCloud, and Dropbox.
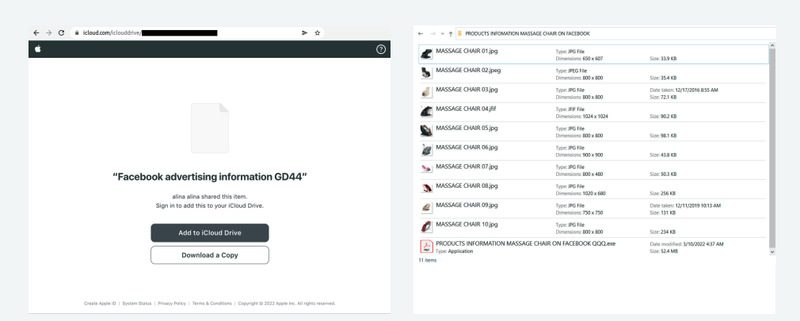
But it doesn’t stop there. The threat actors can also use LinkedIn to promote the archive file containing the malicious payload.
Once it sets root, it allows the attacker to take over any Facebook Business account. Any browser is the key to this campaign’s success.
The malware scans the likes of Microsoft Edge, Brave, Chrome, or Mozilla Firefox and harvests stored cookies and access tokens.
Not only that, but it also steals information from the victim’s personal Facebook account, including email address, name, user ID, as well as name, of course.
A New Info-Stealer: Facebook Users Beware
As the report states, the attack is targeting countries such as the Philippines, India, Saudi Arabia, Italy, Germany, Sweden, and Finland.
Yes, it’s global and expanding fast. Whoever is affiliated with a Facebook Business account should take proper precautions immediately. We advise them to set their access permissions and enable all possible security measures.
For those who use Discord and Telegram, make sure that you don’t trust any message your receive. Stay vigilant, stay safe.





