Mars Stealer Malware – A Malicious OpenOffice Ad Campaign
In the world of cybersecurity, when certain malware shuts down, another one is bound to emerge – full scale. Back in 2020, the Oski malware ceased to exist, giving users some comfort. However, this didn’t last long as the shut-down malware was reimagined/redesigned as the new Mars Stealer.

With new capabilities, Mars Stealer has shown how dangerous it can be. Unfortunately, the malware started off with a bang as security experts have spotted its first notable large-scale campaign.
Mars Stealer is now targeting users through OpenOffice Google Ads advertising. In other words, the threat actors behind this are paying their way to the highest ranks within Canadian search results.
“What Goes Around Comes Around” is a saying we all use, but what does it have to do with the Mars Stealer Malware? You’ll find out in the following article.
Mars Stealer: An Out-of-this-World Malware
Mars Stealer is relatively new, but it does promise to become the springboard of numerous new campaigns. Why is that? Well, first, cybercriminals are always looking for new methods to infiltrate their victims’ systems.
After the Raccoon Stealer shut down (Mars Stealer operates similarly), these threat actors started looking for an alternative. But that’s not the only reason.
It is an alternative, but it’s also available at a reasonable price, which makes it more popular in the cybercrime world. Currently, the Mars Stealer can be purchased at affordable prices in the range of $140-$160 within hacking forums.
Now, the new malware is getting very popular and hackers are using it in all kinds of malicious campaigns to lure new victims. Recently, threat analysts at Morphisec reported a large-scale using Google Ads advertising to promote OpenOffice.
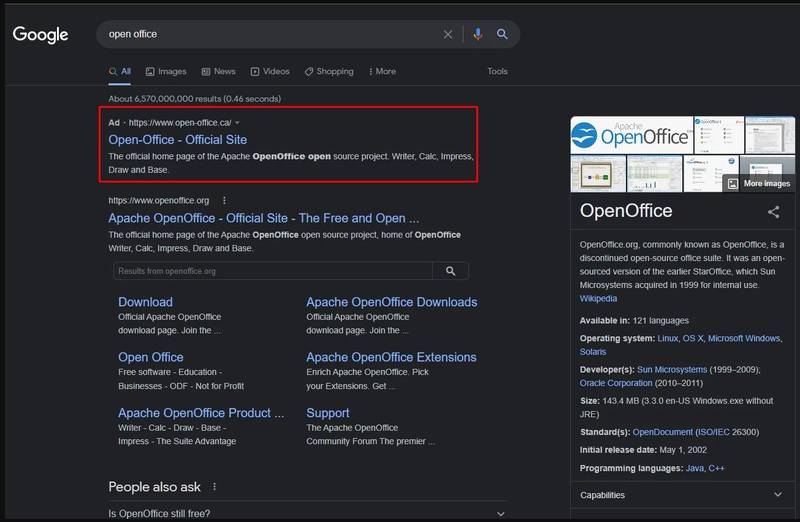
The question is: Why OpenOffice? You see, back in the day, the open-source office suite was pretty popular – not so much now.
Users around the world operate with LibreOffice nowadays, and cybercriminals know all about that. If they choose to mimic a popular service like LibreOffice, chances are their fake website wouldn’t last long due to numerous reports.
Therefore, they targeted OpenOffice, which has a respectable number of daily downloads in hopes of fulfilling their task without stumbling upon any obstacle.
Malware Karma – Everyone’s Exposed
As we mentioned, the threat actors created a fake page to mimic that of the official OpenOffice one. The resemblance is uncanny, but if users are tech-savvy enough, they can pinpoint the difference.
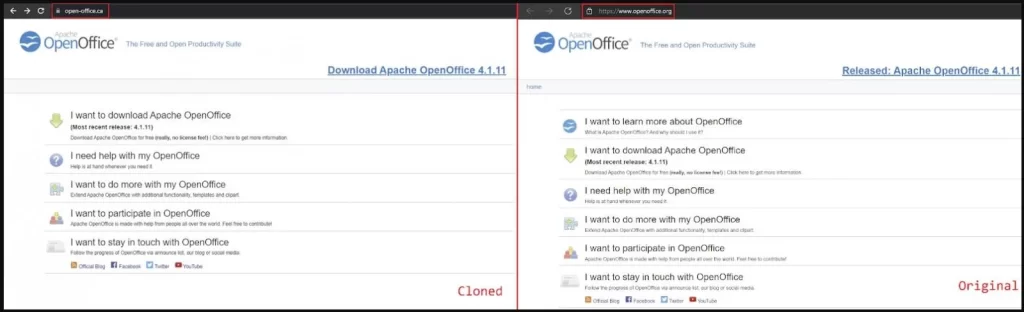
The fake website is well promoted and does appear on the first page in Canadian search results. Once the victims are in, the download pack they get includes the Mars Stealer along with either the Babadeda crypter or the Autoit loader.
That’s when everything goes south. The victims infect themselves and their data goes out in the open. Emphasis on “In the Open” as a slight misconfiguration causes an exposure in the victims’ ‘logs’ directory, granting full access to any visitor.
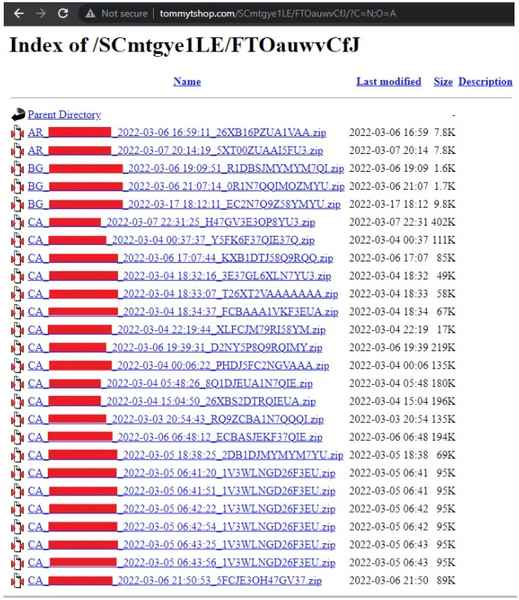
The information that the threat actors harvested is pretty critical as it includes browser extension data, credit cards, IP addresses, country codes, browser auto-fill data, as well as timezones.
However, here’s where Karma plays a huge role in this equation. While infecting their victims, the threat actors have infected themselves as well with the Mars Stealer during the debugging process.
In other words, their sensitive information is also out there for everyone to see. And thanks to that, the researchers were able to figure out a lot of things about them.
Apparently, the attacker is a Russian speaker. Not only that, but the researchers were able to discover the stolen credentials used to pay for these Google Ads, the threat actor’s GitLab accounts, and so much more.
Because the threat actor infected themselves with their copy of Mars Stealer during debugging, their sensitive information was also exposed. Isn’t that right Corpsoft?
OpenOffice Mars Stealer – Everyone’s on the Same Sinking Ship
It’s well known that threat actors that focus on injecting info-stealers are heavily focused on cryptocurrency assets.
According to researchers, this has become a very popular practice, targeting the likes of MetaMask, Coinbase Wallet, Binance Wallet, Math wallet, and more.
We ask you to always be vigilant when it comes to what you download on the internet. Make sure to go to the official download page manually, you don’t need Google to direct you. Stay safe.





