What Are Proxies and Should You Be Using Them?
Today, I would like to talk about proxies. You may have heard of them, as there are hundreds upon hundreds of them — free and premium versions. In fact, even in your internet settings, you will definitely find an option called ‘Proxy.’
What Are Proxies? Should We Use Them?
Whether you know anything about them or not, you are about to learn what they are, what are their uses, their advantages and disadvantages, but also their dangers, and more. For now, however, let’s start with the basics. Here’s everything you need to know about proxies and whether you should use them or not.
Proxies Explained – Content Index
In simple terms, a proxy is a gateway between you and the internet. But that’s not enough to understand the term. That’s why, I made this guide to shed some light on what proxies are, what they do, and whether or not you should use them. Here we go.
- What is Proxy – A Comprehensive View
- Types of Proxies – The Main Six
- Web Proxies – A Better Look
- Proxies – The Who and the What
- Pros and Cons of Using a Proxy
- Proxies – Privacy and Biggest Dangers
- Proxy Detection Method
- Tips on How to Protect Yourself Online
- Top Proxy Alternatives
- What are Proxies – Conclusion
What is a proxy?
 In simple terms, proxies are tools used for achieving online anonymity and bypass censorship and geo-restrictions. This does not establish anonymity ever time, though. There are many different types of proxies and proxy servers, and we will talk about them in a moment, as well.
In simple terms, proxies are tools used for achieving online anonymity and bypass censorship and geo-restrictions. This does not establish anonymity ever time, though. There are many different types of proxies and proxy servers, and we will talk about them in a moment, as well.
The first thing that you should know is that they act as your window in the outside world. Imagine being inside a windowless room, which represents everything that you can access on the internet within your own country.
Everything that yours or other countries don’t allow, such as censored materials, geo-restricted content, and alike — is on the outside. By using a proxy, you are installing a window in the wall of the room, which allows you to view this content as well by becoming semi-anonymous.
However, it all comes at a cost, and I’m not only talking about the money. I will explain that as well, but first — let us see what types of proxies there are.
Different types of proxies explained
Proxies have been around for quite a long time now. The problems such as censorship and online restrictions have troubled people for years, and proxies were invented to resolve those issues. However, by using them, you are only halfway towards reaching a real solution.
During their history, different types of proxy servers were invented, including:
Web Proxies
These are mostly used for filtering content. This type of proxy often keeps logs, keeping information on which websites you are accessing and how much bandwidth you use. Your traffic goes through this type of proxy if you set it up in your browser.
Keep in mind that logging is not always the case, and it all depends on the proxy’s privacy policy. Also, note that ‘web proxy’ can be taken as a sort of a general term. For example, both hostile and anonymizing proxies can be web proxies.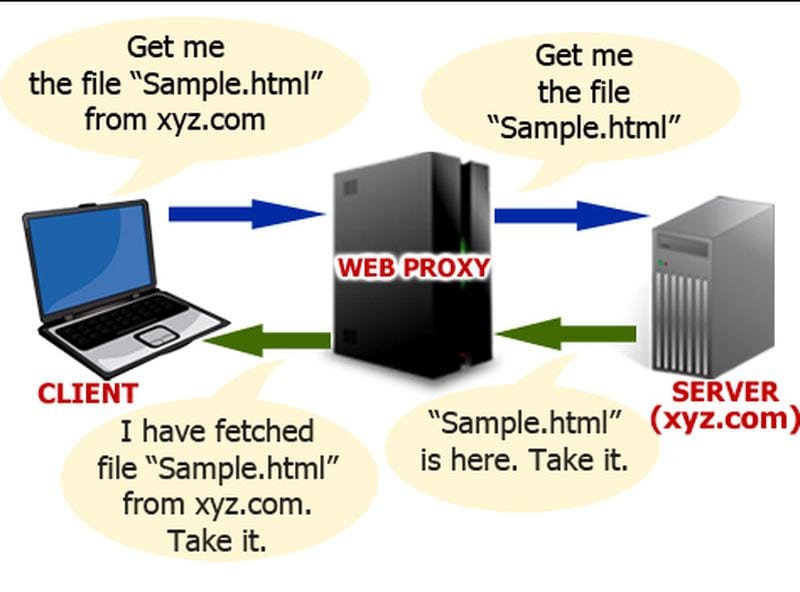
Hostile Proxies
A type of proxy that captures data about web pages that you visit and forms that you fill. Your traffic is mostly forced through this type of proxy, and it is not safe to use them, as they log your information. Your traffic often goes through this proxy if your device gets infected with malicious software.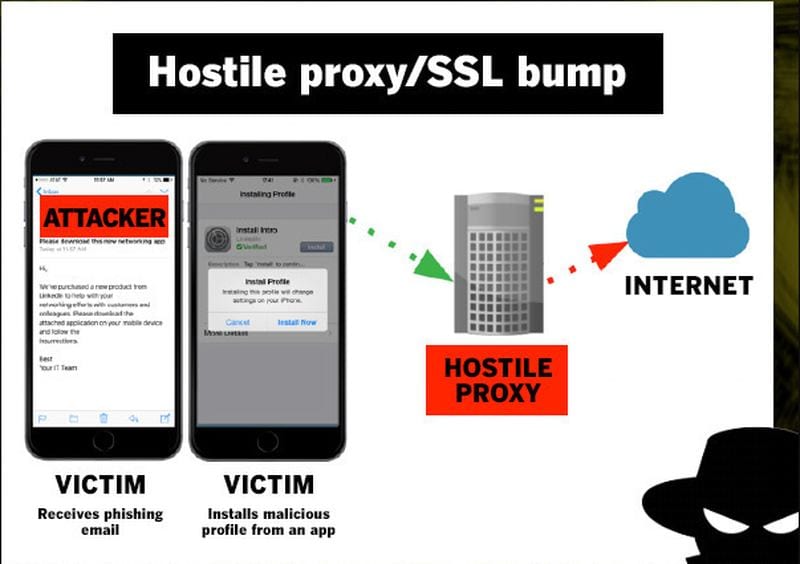
Caching Proxy Servers
These are servers that can speed up requests. They save all your Internet requests, “Both using DNS queries and HTTP queries,” and simply copy the resources that are often used. This improves the bandwidth and the overall experience.
Why? Well, since repetitive content is fetched from the caching proxy and not the website, the content is requested from. This type of proxy server should only be used when it is a homebrew proxy server. In other words, only you can see the cached content and not a third party.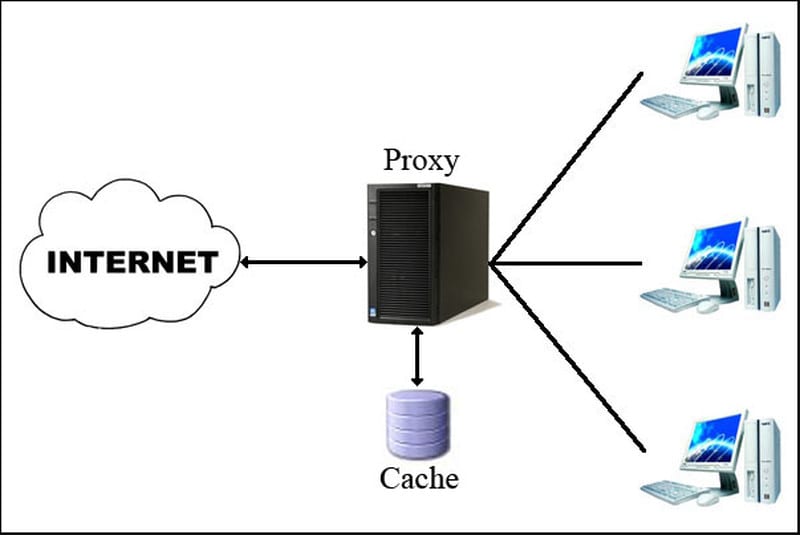
Anonymizing Proxy Servers
This type of proxy makes your internet browsing anonymous, to the websites you request information from. However, as with other proxy servers, the owner of the anonymizing proxy server does still have access to your information.
However, in terms of proxies, it is the closest thing to the anonymity that you can get to with a proxy. Again, to establish this type of anonymity, it is best if you set up such a server urself. Yeah, you can configure DNS on any device effortlessly on your own.
Transparent/Interception proxy
This is a proxy ISPs use to intercept your traffic, which is then forced through the proxy. This can lead to several issues, such as internet throttling, eavesdropping on your actions, recording your online behavior, and increased censorship.
You can check for transparent proxy interceptions with this advanced proxy detection tool. Just use it to check periodically and find out if someone is listening.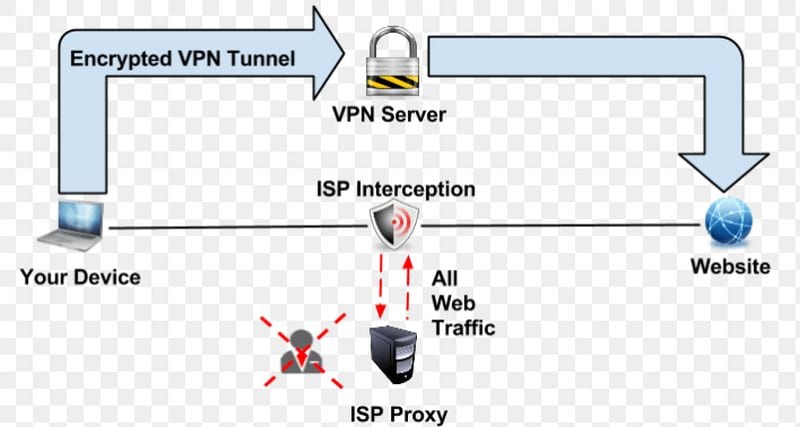
SmartDNS Proxy
With this type of proxy, all you do is change your DNS address. Once you do still use your own IP address for most of your web surfing. However, based on how many streaming channels Smart DNS proxy unblocks, you will get a lot of geo-blocked content. For example, once you change your DNS address, you can access BBC Iplayer or USA Netflix, even if you are not in the UK or the USA.
The way this works is due to the Smart DNS Proxy service taking your DNS queries and sending you through their services instead of you going directly to the website you are requesting. This, in turn, allows your traffic to appear geographically as coming from the Smart DNS Proxy server.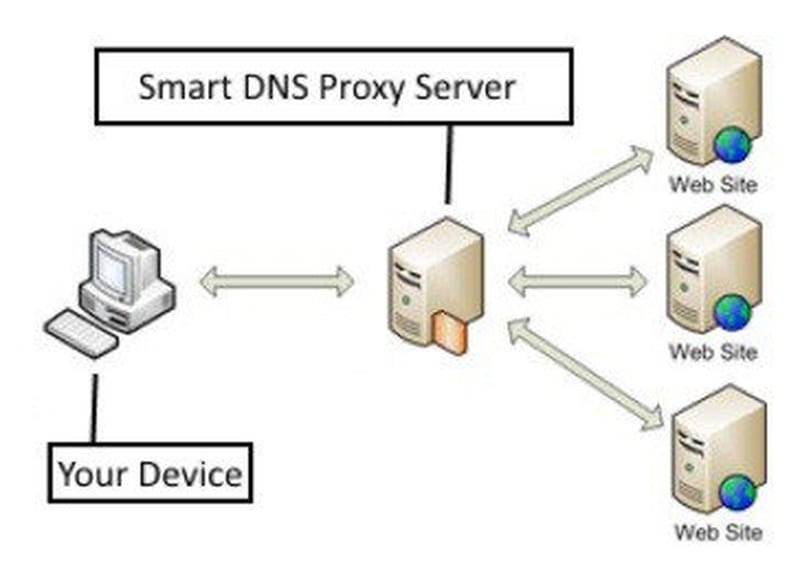
Web proxies, is that it?
There are other types, but these are the main ones that you should know about. Obviously, they come with quite a bit of a flaw, which is storing most of your information. Proxies are not tools that you can use to achieve true anonymity or any type of security online. However, they do allow you to bypass restrictions if you are not concerned about online privacy and simply wish to avoid restrictions.
Proxies, the Who and What?
As I explained already, proxies can be very useful when it comes to accessing foreign or censored content. In essence, they hide your IP address from a service that you are trying to access through them.
When you enable a proxy, your traffic passes through it, and it acts as a shield that protects you from being exposed. Any information request that you send — such as trying to access a website — you send it to the proxy server. The server then asks for the same information from the website, and after receiving it, it sends it on to you.
In other words, a proxy is an intermediary between you and the service that you are trying to access. That way, the proxy hides your IP address — your online address — from these services. That prevents the exposure of your browsing logs, your location, and your identity. One example of a good and reliable that offers a 7-day free trial is Unlocator. However, there are other providers that can help you out, most of them are VPNs that do offer Smart DNS services.
As for proxies, which you should avoid, it all depends on what your preferences in terms of privacy are. Always remember to check out their privacy policies, user comments and reviews, and what exactly they offer. That should warn you in time if the proxy is as good as it claims, or if it tries to log your activities.
Pros and cons of using a proxy
Obviously, like everything else, proxies also have their share of advantages and disadvantages. Here are some of the pros and cons that you should be aware of when using a proxy.
Pros:
- Remain anonymous
- Protect your privacy from websites and services that you visit
- Hide your geographical location
- Gain access to censored or geo-restricted content
- They don’t slow down your internet speed “If a proper caching is used”
- You are protected from malware if the proxy is set up to block malware types. As the data doesn’t interact with your system directly.
Cons:
- Proxy still sees your IP address and knows who you are
- Proxies rarely use encryption. Some proxies do encrypt the traffic between your systems and the proxy servers. That, however, reduces your bandwidth speed.
- The best proxies are premium solutions, meaning that you will have to pay to use them
- No true anonymity or data protection since the proxy operator can see your data.
- A proxy could be run by a malicious party that can steal your data and/or infect your device with malware.
Issues with Proxies: Privacy and Biggest Dangers
 For all their benefits, proxies come with quite a few dangers and risks. I have already pointed out that your information is not safe from the proxy itself, as the service is recording it.
For all their benefits, proxies come with quite a few dangers and risks. I have already pointed out that your information is not safe from the proxy itself, as the service is recording it.
Depending on the service, they do so for various reasons. Many of them are only recording your details so that they could provide a better service, although this is likely only the case when it comes to premium proxies.
The situation is more complicated when we are talking about free services. Free services do not get the money from you, so they need to make it in another way to pay for all the bandwidth, server maintenance, and alike.
They might choose to bombard you with ads, or they could sell the information they are storing. That makes proxies pretty much useless if your goal is to improve your privacy and online security.
The only benefit from such services is the fact that you can still use them for accessing content that you could not see without a proxy. However, there are alternative solutions that could provide you with a better and safer service.
More Dangers?
There are also malicious proxies that are set up by online criminals, hackers, and alike. These are always free for you to fall into their trap. They let you use their proxy, while they are exploiting your privacy, steal sensitive data, and infect your computer with malware. They might even be able to decrypt your passwords.
In other words, you must be extremely careful with free proxies, and never use them to access things like your online bank account, PayPal, and alike. You can never know who owns the proxy, or who might be intercepting your traffic.
There are hundreds of services out there, so rooting out the bad ones is extremely difficult, especially since it is easy for them to come back rebranded.
How to Detect a Proxy?
 As you likely understand by now, proxies can be very useful, but also very dangerous in the wrong hands. Most people who use them just want to achieve some level of anonymity and privacy, but there is a certain percentage that has a bit more dishonest intentions.
As you likely understand by now, proxies can be very useful, but also very dangerous in the wrong hands. Most people who use them just want to achieve some level of anonymity and privacy, but there is a certain percentage that has a bit more dishonest intentions.
Fraudsters and scammers are known for using proxies, as they do not slow down their internet that much but can still let them use spoofed IP address to hide their real location.
By doing this, they don’t have to worry while scamming people, and they can effortlessly perform credit card fraud or bypass restrictions. After the misuse of proxies became apparent, developers have come up with proxy detection services that you can use for detecting proxy users.
Detection Services – Examples!
A lot of companies, e-commerce websites, credit card merchants, and alike are using them these days, to protect themselves and their businesses. Proxy Detection Services such as FraudLabs and MaxMind are among the most popular ones, as they can detect a spoofed IP. Some of these services even have web versions, which allow instant detection.
These detection services work simply enough — whenever you access a website, it records your IP. If you use a proxy, it will record the IP of that proxy. Since many people use proxies all over the world — their IP addresses get much more exposed and are easily recognized and stored in a database.
So, when you use a proxy to enter a website, the site records it, and Proxy Detection Service compares it to its own database. If there is a match, the Proxy Detection Service reports it to its own user.
If you want to detect whether you are behind a proxy, even though you never did use one, you can use this tool.
A Few More Methods to Protect Yourself Online?
I know this article is about proxies, but since we did open this worm box, we might as well mention a few more security issues.
The first thing to note is that you need to remember always to protect yourself while surfing the web. Malicious websites, ads, and other traps are everywhere these days, and the last thing you want is to get your device infected.
Now, as you may know — antivirus software is a pretty good way of keeping your PC safe from most known viruses and malware. You can also use anti-malware software, which specializes in different types of malicious threats.
However, what you may not have known is that antivirus software already does have features that can protect you from malicious sites. These features may differ, but in some cases, an antivirus program may be relying on a proxy to keep you safe.
Chrome’s Enhanced Security
Similarly, if you are a Google Chrome user, you will benefit from their protection tools. The protection applied means that if you are ever about to enter a malicious website — the chances are that Chrome already has data on it stored in its database.
If that ends up being the case, it may issue a warning to you. Thus, it will prevent you from continuing unless you really want to visit a certain website “I strongly suggest not doing that.”
Google constantly works on improving Chrome’s security, performance, and other similar features to keep you, as a user, safe. Of course, that doesn’t mean that you should let your guard down. There are always new threats, and Google cannot always process them in time. It means that it pays to be vigilant and to use security solutions like antivirus, antimalware, and of course — proxies and other similar technologies.
And, when it comes to choosing the right proxy, don’t forget to investigate any proxy you may be interested in before using it. Check out its privacy policy and investigate its website.
Some fake proxy services set up by hackers could steal your data or infect your computer with malware. It is not always the case, but when it comes to your security — it pays to be cautious and even a bit paranoid. Remember, the alternative can be much worse.
Proxy alternatives
While proxies are not among the best ways to keep your anonymity online, there are a few alternatives for you to turn to that will keep you safe. Two proven methods are guaranteed to let you keep your anonymity intact. If you don’t know what I’m referring to, they’re the Tor browser or a VPN.
Tor Browser
 The Tor browser is an anonymous browser that lets you keep your identity hidden and avoid being tracked by websites, hackers, governments, or pretty much anyone else.
The Tor browser is an anonymous browser that lets you keep your identity hidden and avoid being tracked by websites, hackers, governments, or pretty much anyone else.
This browser uses its network, which is comprised of nodes (computers) that are located all around the world.
However, these computers do not belong to some company or service. Instead, they are owned by other individual users who contribute to the network.
When you use Tor, you also use this network to access websites. However, the anonymity part comes from the fact that your request for information gets rerouted, and it jumps from one computer to another.
It does this hundreds or even thousands of times until the path it makes is so complex that no one can ever determine who sent the original request.
Of course, this is all done in a few seconds, meaning that you won’t notice a delay longer than that. But, the negative side is that the delay is there, which makes Tor a lousy solution for downloading or streaming. All the information that you have requested needs to travel just as long a path back to you, which is terrible when it comes to watching videos, movies, and alike.
This is where the second option gets its ability to shine.
VPNs
 VPNs, or Virtual Private Networks, are apps issued by VPN services. These apps allow you to protect your identity and privacy completely.
VPNs, or Virtual Private Networks, are apps issued by VPN services. These apps allow you to protect your identity and privacy completely.
Similarly to proxies, they will hide your real IP from the websites that you are visiting. However, they do so by allowing you to connect to their own servers located all over the world.
Once you connect to one of these servers, you get assigned an IP address tied to that server and its physical location.
This lets you appear as if you reside in the same place where the server is sitting. Meanwhile, your own IP address is cloaked from view.
But, unlike proxies, VPNs don’t stop there. They almost always use security protocols to create a secure tunnel and allow your traffic to flow through it, hiding it in the process. This allows for encryption, which makes your traffic completely unreadable. So, even if someone manages to get their hands on it — they won’t be able to tell what they have.
The Main Features
This is where things get a bit more complicated, as there are also many VPN services out there, and each comes with its own set of additional features. Some have none; some have many. Even these three main features that define a VPN — a server network, security protocols, and encryption — can vary in strength and quality.
VPNs are a bit slower than proxies since they are encrypting all of your traffic on the go. However, with constant development and advancement of this technology, many of them can now offer fast servers that still allow high speeds for streaming, torrenting, and even online gaming.
But, best of all, a lot of the top-quality VPN providers won’t log any of your information at all. Make sure to use a VPN provider with a strict no-log policy. But, you must still be careful when choosing a VPN, and never use a free one, as they’re almost always just as bad as proxies.
If you don’t know your way around, I recommend using the likes of ExpressVPN, BulletVPN, or NordVPN. These three providers offer premium services and top security in the industry. Stay safe, pick a credible VPN service.
Conclusion
I did cover what proxies are and the different types, as well. Depending on your needs, proxies can be a good or a bad thing. Either way, always make sure you look for signals of your data being logged. Again, if you are suspecting you are behind a proxy, or you just want to check that, use this tool.
If you are looking for real anonymity, it is better to turn to Tor or VPNs. Proxies are simply not good enough with all the tracking technologies available today. How useful was this guide to you? Did you learn new stuff? Tell me all about it in the comments.





