Spear Phishing: What is It and How to Spot It?
Spear phishing is an increasingly popular form of security breach used against all kinds of online accounts. It includes everything from private individuals to corporations. It’s a rather deceptive form of an online scam, which is hard to figure out. This is because it specifically targets the weak elements in any security setup.

So, you may get an email forged in the name of your PayPal account. If it carries a link and you open it, then you might expose yourself or your organization to a hacker’s trap. If you want to avoid that and stay safe online, you must first know a few things. Let’s have a look.
What is Spear Phishing?
 Spear phishing is basically a more sophisticated or streamlined form of online scam. It specifically targets people after they have been vetted.
Spear phishing is basically a more sophisticated or streamlined form of online scam. It specifically targets people after they have been vetted.
It is usually done via social media stalking or other forms of data gathering. Once the information is compiled into a profile, the hacker will use it to pitch a highly developed phishing email.
Now, if the target opens the email and clicks the link, they might lose their data. This can grant the hacker access to any account which the credentials lead to.
The problem is very serious. Over 80% of all malware attacks come from phishing attempts using different variations of social engineering techniques. If you fall victim to one, the results can be chaotic.
Ubiquiti Networks Inc. was one of the many victims of Spear Phishing. It’s a US network technology company for service providers and enterprises.
Back in 2015, the company lost an approximate of $46.7 Million due to a Spear Phishing email. As reported, the incident was a result of someone impersonating an employee and sending fraudulent requests to the Company’s finance department.
Naturally, it is a very effective means of breaking into secure accounts, and it is also hard to spot. So, it is important for you to understand how you can avoid being spear fished. Prevention is better than cure!
How to Spot a Potential Spear Phishing Email?
Spear phishing attacks have become more and more common these days. The lack of knowledge of common office goers or private individuals makes these attacks more successful than broad-spectrum hacks.
They are also incredibly hard to detect unless you know the telltale signs. Here are some measures you can take against opening any potential spear phishing email:
Keep Devices Updated
Phishing attacks work in many ways. Some of them ask you to enter your login details for PayPal or your chosen bank. Others can also inject malware code into your device.
There are several other back end measures by which your device might get compromised. One of the best ways to avoid this is to simply keep your device updated.
Usually, companies will issue regular updates so that many of these system weaknesses can be covered. It is a baseline measure, however. You should not rely only on it to prevent spear phishing attacks.
DMARC Authentication
DMARC (Domain-based Message Authentication, Reporting, and Conformance) is a smart measure used by companies to authenticate email sources.
Such a system can be very useful for both internal and external authentication. Basically, the DMARC system uses domain authentication to validate the source of emails.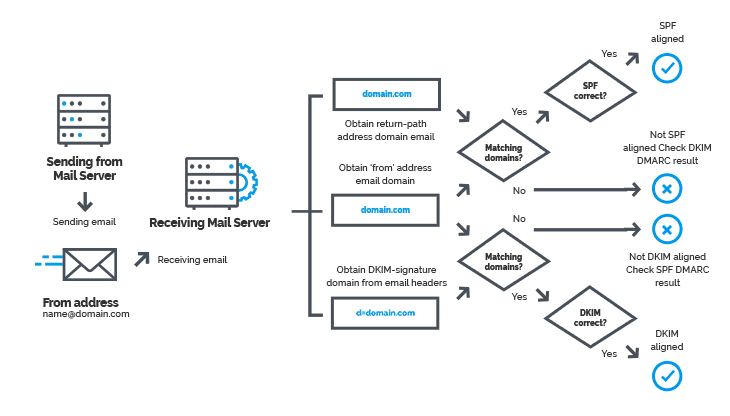
More specifically, SPF (Sender Policy Framework) and DKIM (Domain Keys Identified Mail). This prevents unauthorized emails from unknown domains from bypassing your spam settings. Naturally, It also lowers the chances of you opening any potential phishing email.
Ensure SSL Certificate
Secure Socket Layer certification is one of the most important base-level protections every website needs to give. So, when you get an email asking you to go to a link, you should check the address bar.
At the left of the URL bar, you should see a locked padlock icon. This shows that the website has an active SSL certification subscription. Now, it is possible to imitate SSL like verifications, but it is rare.
So, you should not rely on it completely. However, it can be one of the many factors you use to verify if an email, especially financial email, is authentic.
Multi-Factor Authentication
Multifactor authentication is one of the most important layers of safety you can find in most online accounts these days. You can find these on social media like Facebook, Google email accounts, and especially financial accounts.
If you are using any online payment services, then it is best to use multifactor authentication to validate any transactions. Usually, it involves your basic email or account password, phone validation, and some other layer of protection.
It is a good measure by which you can prevent financial theft. It also keeps all kinds of essential data safe. If an attempt is in place, you’ll at least be notified so you can do something about it.
Use AI
Artificial intelligence has made a lot of positive strides in cybersecurity. One of the most important deployments of this technology has been to cover lapses in system security.
If you are concerned with phishing attacks, then using the right AI-driven antivirus software is a good choice. That can help you potentially identify, scan, and avoid spear-phishing emails.
It can also prevent unauthorized injection of code into your device. It applies both to laptops or mobiles/tablets and can help you secure your device against other threats as well. You’ll see such incidents very common among Android users in particular.
Suspect Grammar
One of the most telltale signs of dodgy emails is faulty English. If an email has bad grammar, chances are it is a forgery. Do look closely at the logo and the fonts used in the email.
It can often expose an email as coming from a compromised source. Bad grammar, in particular, is a telltale sign of fake emails.
If you are then asked to click a link, then you should verify the email at its source. Do not click on anything or respond with any information at all.
The Use of Virtual Private Networks
Phishing scams can pose a real danger to your life and financial stability. They can appear at any time in your inbox and take you by surprise. Aside from the technical aspects of keeping yourself safe, you should also keep your eyes open for signs. Further, you can use software like antivirus and VPN to protect yourself.
The second type is often very useful for getting the right mix of security and convenience to protect your online privacy. Since phishing scams are predicated on personal info, you should use your VPN to cover your regular browsing. As a result, it will minimize your exposure and give you greater safety from all online scams taken together.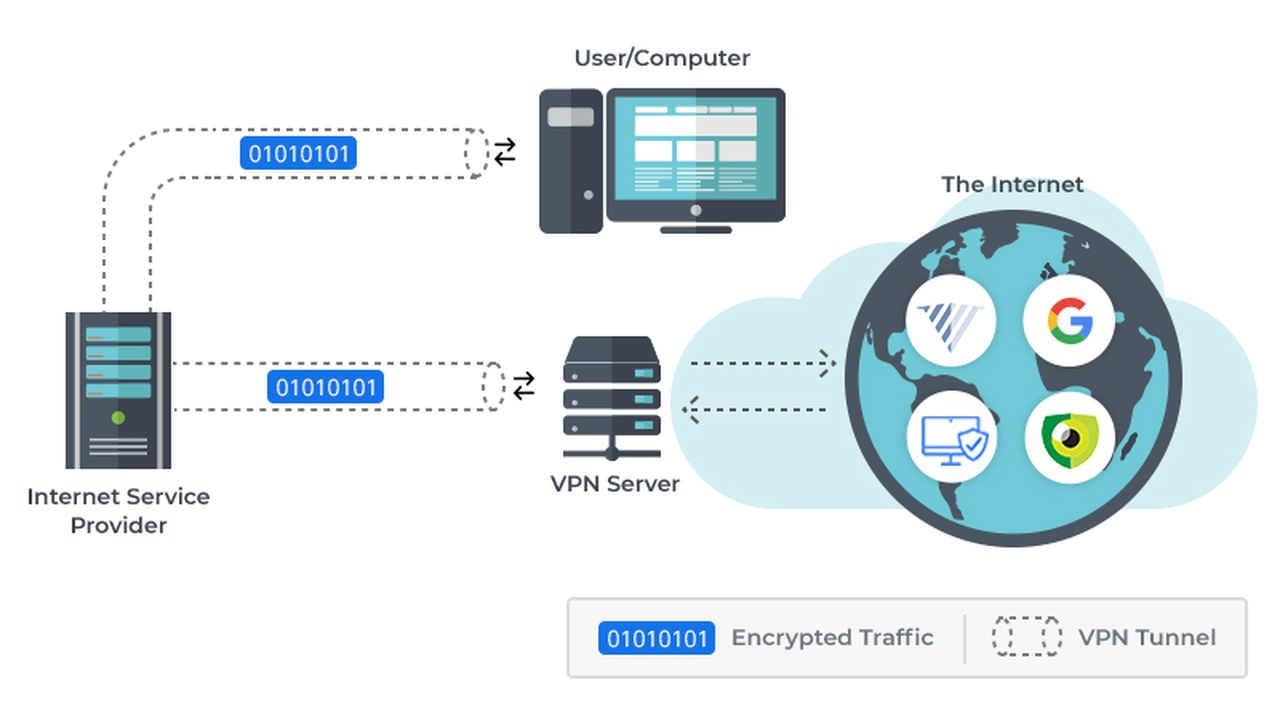
But make sure you get a premium one as free ones are also pretty dangerous when it comes to online privacy and security. So, here’s how you can set up a VPN on your device:
- Create an account with a credible VPN provider.
- Get their app and install it on your device.
- Activate the app and sign in with your username and password.
- Connect to a server of your choosing.
- You’re now completely safe and anonymous.
The Easiest Solution – Just Don’t Click the Link
Phishing emails are a pain, I know. But the best and most effective solution of them all is not to click the link, to begin with. When you get an email with a link in it, don’t start second-guessing and stuff, just avoid it from the start.
In case you don’t know they look like, here’s an example.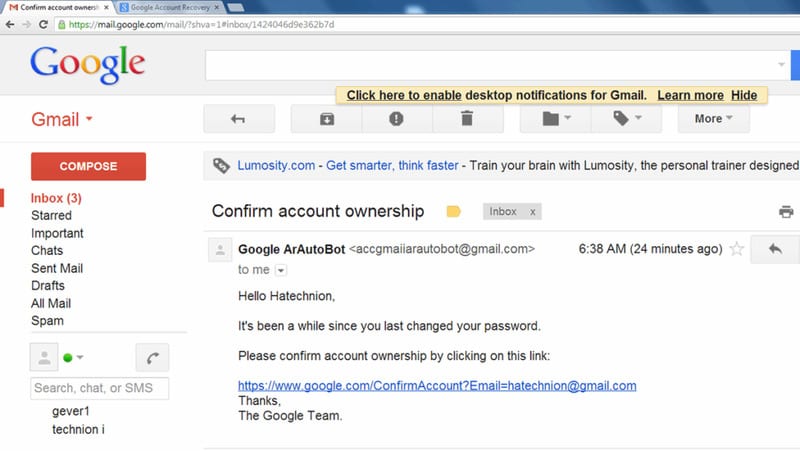
Whether it’s legit or not, take a few extra seconds and visit the official website directly. There’s no harm in doing so. At least, you’ll know that whatever you submit or click there, is completely safe and legit.
Spear Phishing Explained – The Final Words
You might be confused between Phishing and Whaling attacks, but they both vary in sophistication and targets. Whaling targets CEOs, CFOs, and other executives. In other words, people in high places with higher access.
Both of them are dangerous, and Spear Phishing might target anyone. You now know what it is and how can you prevent it. Go through the guide carefully.
By the end of the day, it’s your private and sensitive information on the line here. So, stay safe. If you have further questions, please don’t hesitate to contact me in the comment section below.





