VPNs in the Spotlight – One Study Raises Numerous Concerns
Virtual Private Networks are cybersecurity tools that gained a lot of popularity in the past decade. With services such as top-level encryption/tunneling, censorship circumvention, and unlocking geo-blocked services, we have no doubts about this rise in popularity. But the question is: Are they as secure as everyone wants them to be?
During the pandemic, VPN downloads skyrocketed in terms of numbers. But still, we have to acknowledge the fact that not every VPN is capable of holding its end of the bargain, especially those that offer their services for free.
Unfortunately, a single security study raised a lot of concern when it comes to trusting VPNs – even premium ones.
These services might come with different vulnerabilities or security issues, including weak security protocols and reliability. So, what does the study bring to the table? Here’s what we know.
VPNs in 2023 – Vulnerable Servers in the Millions
As we mentioned, a VPN has been a very handy tool to maintain elevated security and anonymity while browsing the web for so many years now.
In basic terms, Virtual Private Networks provide an encrypted server and hide your IP address from third-party entities such as ISPs, governments, and, of course, would-be hackers.
This goes specifically to those using public or shared Wi-Fi, as their data is kept private from any prying internet eyes. However, apparently, in 2023, these granted privileges have been put into question.
The study performed by researchers from the Max Planck Institute for Informatics swooped the internet for VPN traffic and found around 9,817,450 reflect that of VPN servers.
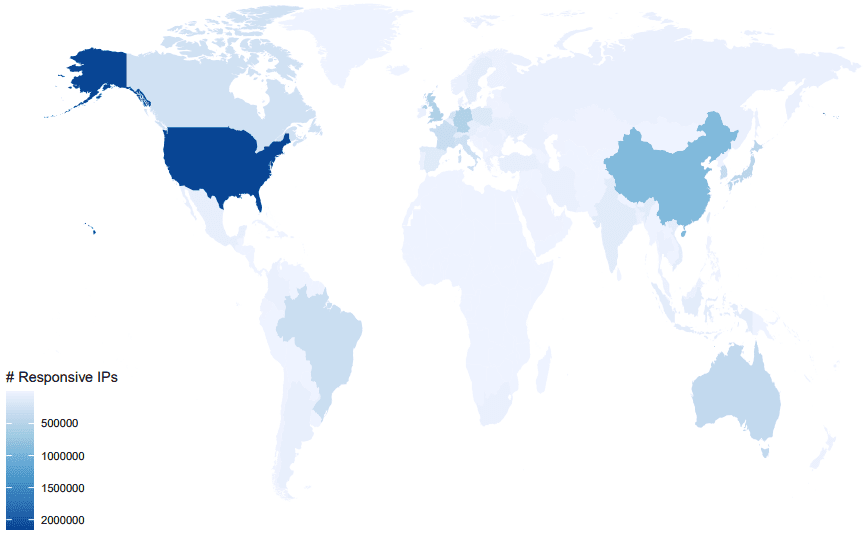
As it turns out, the servers we all trust to route our data through were found to be completely vulnerable to cryptographic flaws like the ROBOT attack (Return of Bleichenbacher’s Oracle Threat).
The introduction of the WireGuard protocol gave tech-savvy users full trust in VPNs in terms of upgrades and adaptability. However, the study focuses on servers that use SSTP and OpenVPN protocols.
OpenVPN is still widely used among providers with a “Completely secure and fast” reputation. Well, that’s not the case here.
According to the study, 7 million of these servers operate using the IPsec protocol, 2.4 million of them use PPTP and just 187k use SSTP.
What’s shocking is that only 1.4 million rely on OpenVPN, which should’ve been the VPN standard protocol. Reputable services should even be using PPTP anymore.
Among the 1.4 OpenVPN servers, about 70% of them operate over UDP, and 30% use TCP – the alternative option.
Flaws Everywhere – Thorough Studies Beget Concern
Basically, SSTP operating servers are not that common. However, even with a small number as 187k, the attack possibility rate is very high.
90% of the SSTP detections can fall victim to ROBOT, which is a highly sophisticated attack that exploits weaknesses in the RSA asymmetric cryptography algorithm.
When ROBOT is in place, the attackers can record SSL/TLS traffic and exploit it for malicious actions later on. They can then decrypt the content of TLS traffic by sending requests to the target server.
A lot of big names fell victim to ROBOT in the past, including Cisco, Citrix, F5, IBM GSKit, Palo Alto Networks, and more.
Unfortunately, servers with SSTP aren’t the only ones considered when it comes to ROBOT and other forms of attacks.
The study states that the OpenVPN servers (1.4 million) are also vulnerable to many types of known attacks. Here’s a list reflects all the findings:
- RC4 attacks: 32,294 servers.
- Heardbleed: 232 servers.
- Poodle: 7,005 servers.
- Logjam: 8 servers.
- FREAK: 31 servers.
- ROBOT: 95,301.
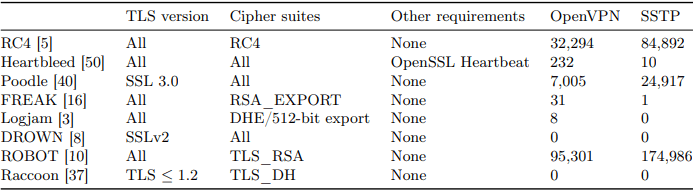
No servers showed any vulnerabilities to Raccoon and DROWN attacks, but we shouldn’t omit the possibilities.
All in all, 134,891 OpenVPN servers can be utilized in dangerous attacks, which is still a high number considering how popular this protocol is among VPN providers.
No Certified Certificates
Moreover, it’s worth mentioning that most of these servers use self-issued and self-signed certificates. But the most worrying part is that a significant amount of them, OpenVPN servers (3.8%) and SSTP servers (9%), were operating using expired certificates.
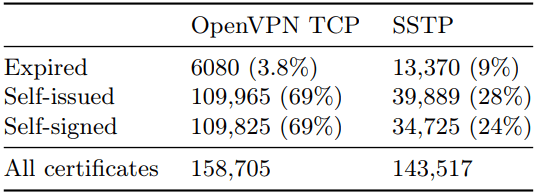
Not only does that make them unreliable to use, but it can also allow threat actors to intercept and manipulate the communication between users and servers.
The study concludes with numerous VPN servers that don’t provide an SNI extension in their TLS handshake.
In other words, users cannot verify the server’s identity. Not only that, but this can also reflect an opening for man-in-the-middle attacks (MITM) and server spoofing.
The Protocols We Trusted, Are Busted!
For a long time now, OpenVPN has been the go-to protocol that most VPNs use. Providers all over the world took it as a standard within their services as it promised security and speed.
This study shows that SSTP is highly insecure. But the shocking part was that the famous OpenVPN can have its risks in the current landscape, which is practically why VPNs that didn’t adopt WireGuard yet should consider a quick shift.




